STOP Djvu Ransomware Decryptor is a free decryptor created by Emsisoft and Michael Gillespie that allows everyone to decrypt files that were encrypted with the STOP ransomware. Currently, this decryptor can decrypt most variants of this ransomware (148 variants). Part of other versions of this ransomware, namely, cases when encrypted files have the extension: .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, can be decrypted using STOP Puma decryptor. Unfortunately, in most cases, it is impossible to decrypt files that are encrypted with new versions of this ransomware (starting from August 2019). If you become a victim of one of these new variants, then at the moment you can only decrypt files that were encrypted with offline keys.
What is STOP Djvu Ransomware
STOP Djvu Ransomware is the most active and widespread ransomware. Like other ransomware, it is designed to encrypt files that can only be decrypted after payment of the ransom. According to the ID Ransomware, to date, more than 450,000 victims have already been discovered, and their number is increasing by approximately 1,500 people every day. The reason for this is that this ransomware is mainly distributed through adware, cracks, free programs and key generators, allowing users to activate paid software. Children, students and many other users, are looking for freeware, download and run it, not knowing that in this way they can allow the ransomware to penetrate on the computer.
Summary
| Name | STOP (Djvu) ransomware |
| Type | Crypto virus, Filecoder, Crypto malware, File locker, Ransomware |
| Encryption algorithm | The ransomware encrypts files using a strong encryption algorithm, which is called Salsa20. |
| Encrypted files extension | .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .djvut .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad, .promorad2, .kroput, .kroput1, .charck, .pulsar1, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .forasom, .berost, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, ,vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, prandel, .zatrov, .masok, .brusaf, londec, .krusop, .mtogas, .coharos, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .stare, .cetori, .carote, .shariz, .gero, .hese, .geno, .xoza, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .noos, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, .kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt, .cdmx , .cdqw |
| Ransom note | In each directory where the ransomware encrypted the files, it drops a new file (ransom demand message). The very first versions of STOP used the following file names: !!!YourDataRestore!!!.txt, !!!RestoreProcess!!!.txt, !!!INFO_RESTORE!!!.txt, !!RESTORE!!!.txt, !!!!RESTORE_FILES!!!.txt, !!!DATA_RESTORE!!!.txt, !!!RESTORE_DATA!!!.txt, !!!KEYPASS_DECRYPTION_INFO!!!.txt, !!!WHY_MY_FILES_NOT_OPEN!!!.txt, !!!SAVE_FILES_INFO!!!.txt and !readme.txt. Starting with the version that, after encryption, added the .djvu * extension, the ransom note had the following file name: _openme.txt, _open_.txt or _readme.txt. The most recent versions of the STOP Djvu Ransomware use only one file name: _readme.txt. |
| Contacts | STOP ransomware developers often change the email addresses that are used to contact victims, the last of them are listed below: support@freshingmail.top, datarestorehelp@airmail.cc, support@bestyourmail.ch, admin@helpdata.top, manager@time2mail.ch, supportsys@airmail.cc, support@sysmail.ch, helprestoremanager@airmail.cc, manager@mailtemp.ch, supporthelp@airmail.cc, helpteam@mail.ch, restoremanager@airmail.cc, restoreadmin@firemail.cc, restoremanager@firemail.cc, helpdatarestore@firemail.cc, helpmanager@mail.ch, helpmanager@firemail.cc , helpmanager@iran.ir, helprestore@firemail.cc, datarestore@iran.ir, datarestorehelp@firemail.cc, datahelp@iran.ir, restorealldata@firemail.cc, restorefiles@firemail.cc, restoredatahelp@firemail.cc, salesrestoresoftware@firemail.cc, salesrestoresoftware@gmail.com, gorentos@bitmessage.ch |
| Ransom amount | $1999, $999 (if paid within 72 hours) |
| Encryption keys | Security researchers have determined that STOP Djvu Ransomware uses two types of encryption keys. The first one is online keys, the ransomware uses these keys if during encryption it has access to the network and can connect to its command-and-control server. These keys are unique to each computer. The second group is offline keys. The ransomware uses these keys if it does not have a connection to its command-and-control server. These keys are the same for different computers. That is, the same key can be used to decrypt files regardless of which computer they were encrypted on. To date, security researchers have found offline keys for some variants of STOP Djvu Ransomware. |
How to decrypt files encrypted by STOP Djvu Ransomware
Depending on the version of STOP Djvu Ransomware, you need to perform different steps to decrypt files. The version of STOP Djvu can be determined by the extension of the encrypted files. Before decrypting files, you need to be 100% sure that the ransomware is completely removed. We recommend that you use several tools (with different anti-virus engines) to scan your computer and remove STOP Ransomware and other malware. Some of the best and free malware removal tools are listed in this article – Best Free Malware Removal Tools.
1. Old STOP ransomware
A variant of STOP ransomware using the extension: .puma, .pumas, .pumax. All known variants of this ransomware can be decrypted using STOP Puma decryptor. Also, with this decryptor, in some cases, files with the following extension can be decrypted: .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT.
Download the decryptor from the link below
https://www.emsisoft.com/ransomware-decryption-tools/stop-puma
Right-click on the downloaded file (decrypt_STOPPuma.exe) and select “Run as Administartor”. You will be shown the license terms, click yes to continue. The program starts, you will see a window, as in the example below.
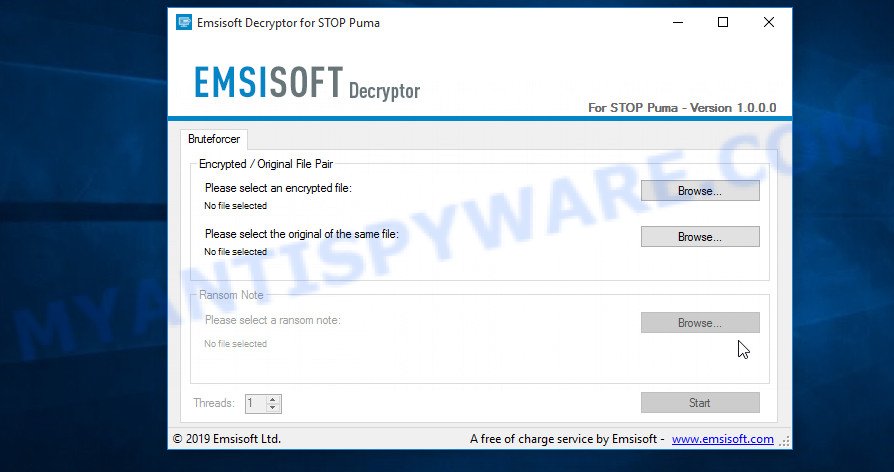
STOP Puma decryptor
As we already reported above, in order to use this decryptor you need one, or better, several pairs of files, one of which is encrypted, and the other is its original version. Having prepared the corresponding pairs, then you need to select them using the corresponding buttons in the program window. When ready, press the Start button. As soon as the key is found, the decryptor will immediately inform you. In some cases, an error may occur while searching for a key, therefore we recommend using several pairs of files to be sure that the correct key has been found.
After the correct key is found, you will be able to decrypt the files. Select the location where the encrypted files are located and click the Decrypt button.
2. STOP Djvu ransomware
A variant of the STOP Djvu ransomware using the extension: .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote.
In order to decrypt files you need to find several pairs of files. Each pair of files consists of an encrypted file and its original copy. File size over 150kb. After you find several pairs of files, do the following. Open the following link in a new window.
https://decrypter.emsisoft.com/submit/stopdjvu/
You will see a page called STOP Djvu Decryption. An example of this page is given below.
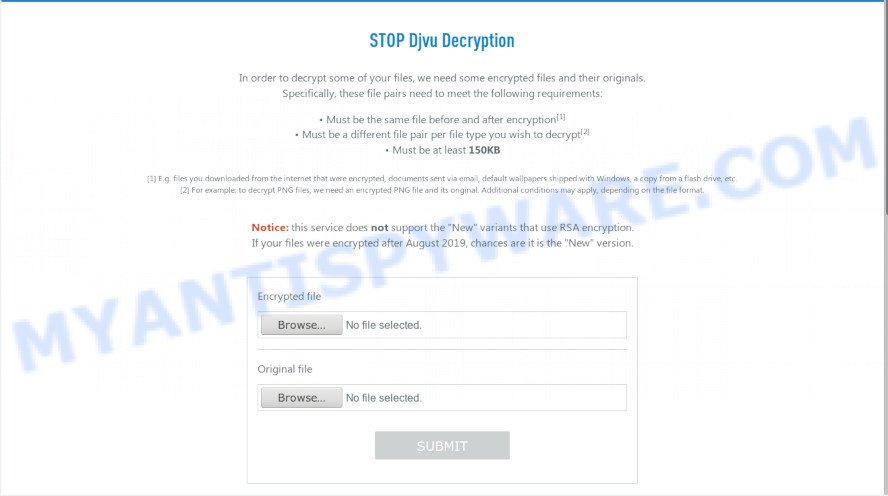
STOP Djvu Decryption
On this page using the Browse button, enter the path to the encrypted file and its original copy, then click the Submit button. After clicking on the Submit button, your files will be uploaded to the server. Then the key search process starts. Please be patient, this process may take some time. As soon as the key is found, an appropriate message will appear on the page and you will be asked to download the decryptor.
Click on the link called “Click here to download the decryptor“. The page from which you can download the decryptor will load. Click the Download button and save the decrypt_STOPDjvu.exe file to your computer.
When the file is downloaded, start it by right-clicking on it and selecting item “Run as Administrator”. When it starts, the Windows can show you UAC Promt, then click Yes. After that, you will be shown the license terms and a small instruction, please read this information to continue.
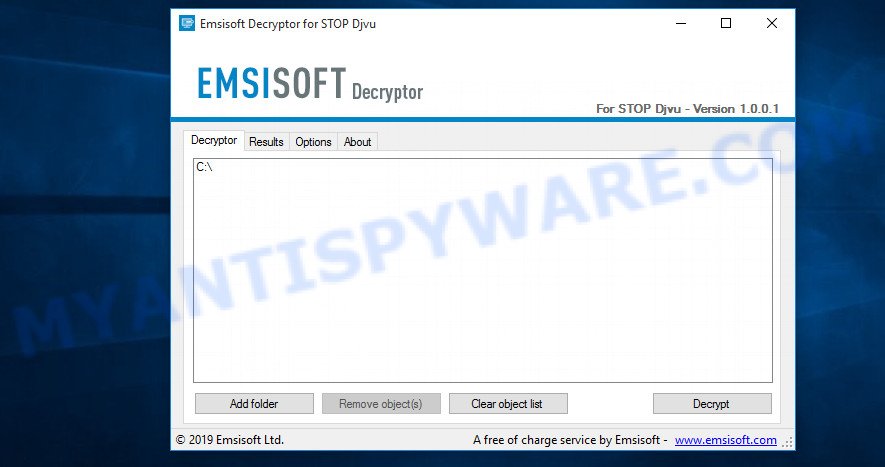
STOP Djvu decryptor
In the main window, select the disk or directory where the encrypted files are located, and then click Decrypt. After that, the decryptor will begin to decrypt the files for which the key was found at the previous stage. If the decryptor skips files, saying that it cannot decrypt them, then you need to again find a couple of files, one of which is encrypted, and the second is its original copy. Then use them to find the decryption key.
3. New Djvu ransomware
The latest version of STOP Djvu ransomware uses the following file extensions: .coharos, .shariz, .gero, .hese, .geno, .xoza, .seto, peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, gcyi, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt. An updated variant of this version appears every few days, the main difference between all variants is the extension of encrypted files. The last variant encrypts files with the .qqmt extension; the personal ID of the victims of this variant starts with 0540.
At the moment, it is possible to decrypt files only in some cases when they are encrypted using an offline key. To decrypt files, download the decryptor using the following link.
https://www.emsisoft.com/ransomware-decryption-tools/stop-djvu
Click the Download button and save the decrypt_STOPDjvu.exe file to your computer. Right click to it and select ‘Run as Administrator’. Confirm permission to run the program by pressing the Yes button. Read the license terms and brief instructions. In the main window that opens, select the disk or folder where the encrypted files are located and click the Decrypt button. If the decryptor skips files without decrypting them, then the offline key for them is unknown or they are encrypted with an online key.
This video step-by-step guide will demonstrate How to decrypt files locked by STOP Djvu ransomware.
Finish words
We hope that the set of utilities and services developed by Emsisoft and Michael Gillespie helped you decrypt all the files. If the decryption of the files failed, then do not forget that there is another way to recover your files – is to use data recovery tools. Details on how to recover encrypted files without a key and decryptor are described in the article:
How To Recover Encrypted Files (Ransomware file recovery).











I tried the new free STOP decryptor that was created by Emsisoft and Michael Gillespie but it was unsuccessfull. it shows Erro: Unable to decrypt file with ID: tQnMlIDzipWHEe9cbjW4TmHwefTSXSXWmxLOBNk8.. … please help me
It looks like your files were encrypted with an online key. There is currently no way to decrypt these files. The only way you can use – is to use programs created to recover files from a hard drive. This article shows how to use such programs to recover encrypted files.
i tried to encrypt the leto files but it shows a error …..Unable to decrypt file with ID: yLPMpAQroN0dKOs3a8xmHSQszSyZhuZdcsletot1
What’s the reason?…Please help
Since your ID ends in ‘t1’, it means the files have been encrypted with the offline key and can be decrypted. It seems that the offline key has not yet been found, so the decryptor cannot decrypt encrypted files. You should be patient, from time to time try to decrypt the files.
unable to decrypt the files ID: 0173HfghPQSZH66B9FYiXd6SyGNAKATvZNI5U7ls5nMqdamQR
This personal id means that you have become a victim of one of the latest variants of STOP ransomware, as well as the fact that the files are encrypted with an online key. In this case, the decryptor from Emsisoft will not be able to help you. Try using data recovery software to restore encrypted files (link).
i have the same problem with .LETO files… is a offline key.. the same for others users here 🙁 ..but can’t decrypt no one…
Unable to decrypt file with ID: yLPMpAQroN0dKOs3a8xmHSQszSyZhuZdcsletot1
Since the decryptor cannot decrypt your files, the offline key corresponding to this ID has not yet been found.
ATTENTION!Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-s1t5wqNfSG
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
gorentos@bitmessage.ch
Reserve e-mail address to contact us:
amundas@firemail.cc
Your personal ID:
0172Hf73y87gsyBvxtYXH4bVmZZdtLoPw6OuMTNzyleSFLj3YCt0h
when will they make it available to decrypt file. with leto virus????
Error: Unable to decrypt file with ID: 6WWM0QaSEPmws2Skr21Ja68bM1tJV8LEDlt1ETT1
Hi Myantispyware team,
This article really helped me for the .derp extention files Thank you…
At the same time dealing the ID problem with .nakw file ….surfing over the net for other solutions…. Thanks again
Andr, it looks like your data is encrypted with an online key. At the moment, these files cannot be decrypted, since only criminals have the key.
I got infection too, here is a message. Please help me to decrypt my file.
ATTENTION!Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-IbdGyCKhdr
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
salesrestoresoftware@firemail.cc
Reserve e-mail address to contact us:
salesrestoresoftware@gmail.com
Your personal ID:
0176Asd374y5iuhldyMHCPVD6OfiejaxXnk3zsfKyrS58yQwWrKHEbxgS
ATTENTION!Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-IbdGyCKhdr
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
salesrestoresoftware@firemail.cc
Reserve e-mail address to contact us:
salesrestoresoftware@gmail.com
Your personal ID:
0176Asd374y5iuhldbWPZL2c71V2K2VBpiMXQGDHlOyrCLJm91bzNOFd3
please tell me what should i install or what will you recommend me
please reply me, i am worry about it , please reply me
Based on your ID (0176Asd374y5iuhldbWPZL2c71V2K2VBpiMXQGDHlOyrCLJm91bzNOFd3), it can be seen that your files are encrypted with an online key. In this case, they cannot be decrypted, since the key is in the hands of criminals. Try alternative ways to recover encrypted files.
How is one expected to have the original file along with the infected encrypted file to use this decrypyor?
There are several quick ways to find a pair of encrypted / unencrypted files:
1. use pictures that come with Windows OS: examples of pictures in the folder My documents/Pictures, desktop backgrounds.
2. perhaps before the files were encrypted you downloaded any files from the Internet. These files remained unchanged on the Internet, and can be used by you to create a pair of files.
Please help! victimed by STOP DJVU .MEKA extension
Your personal ID:
0178Asd374y5iuhldnrmAvm4SKxHFYRBnhyLINwRGl4FvjnE6kg7zeBgf
PBols, your id means that your files are encrypted with an online key. Currently, such files cannot be decrypted. The only way for you to recover the contents of encrypted files is to use alternative methods. More details here.
SIR I HAVE REMOVED THE VIRUS BUT I CAN’T DECRYPT IT ,BUT IT COMES AS UNABLE TO DECRYPT WITH ID BpNeQLDlV2KlILQonqNE0rWSIOS3nTb77HIXnffu, GIVE A SOLUTION FOR IT PLEASE
It looks like your files were encrypted with an online key, in which case the decryptor will not be able to help you. I also advise you to look at file ‘PersonalID.txt’ (that is located on disk C, SystemID folder), maybe several IDs are listed there. If one of them has ‘t1’ at the end, then some of your files are encrypted with an offline key. Such files can be decrypted. Also try alternative methods of data recovery, maybe one of them will help you.
I need help. Suddenly, all my files were renamed, they now have the extension ‘.lokf’. I also found a file that says that my files were encrypted. Google search does not find any free decryptor. Can you tell me if there is a way to decrypt .lokf files?
Dear all,
Yesterday I got .mosk virus and the ID is 0180jYgs9f6sodez3BD5petVcYyY7Sbgz5lsiX8fdQ2ZKw8i2odE . I tried with this tool but it not worked. All my important data was encrypted and I’m so sad. Please reply and help me. Thanks so much.
I already decrypted my files encryptded by malware with MOSK extension
online key as per below, hope it may be helpful to develop encryptor on it for every victims
—–BEGIN PRIVATE KEY—–
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDAS1A4nwZ+UZrx
s2nWWc4JmCUlsLEKn5ZkiY4wuYigacknYG+/HcOccblMQunAR6k+VU8UrHYG3eY9
dVyKRtwMwW4uzK/Cu3B/n6+xCGUDnsj6CgMjOnFQ2GwGfLsdaFPvtQys3YQwWDXZ
6jpnAu0v0+ekdWkwmf/N+WivTFzFkjDyBlZsfEOL5hbKhoPYU8jRinymoaeLpVlC
OZv3JZf5AEOC3ImD9rWcSKXf5xET0tpNUkO5YLY4n7uvugHLIkv/hXpCyllOJyeh
m+KpkccX1EgEbngPjXqd9cPB8Uc2iShwVqJhKkzBnzuXzQezp6Wu44lDtF6PTEVx
9xg4U9krAgMBAAECggEBAJtOeJ0yeykcubrKwAlagNko45+8RFEjMXFD0+6wepOs
vMUr0zUVUf6RrynTxT0B48QvXG6DF9RV9fXfSv13W5SFyXrM4IuznZnGHD0sXYF+
Bi5EVeJm+kxkb2MR7IJE1737iSA4zOHK7LtyvPaj23NMf4NJPMr/JiZycMVcNHVw
QzRxvj6x5TRpcTxNICCR8HJEBLcg57+xAyeOflyAbnOvu+Xkr5igJkoYQoZAugZl
ig47fx0yJSgbyiVbUGJfgapKafzPRRdtPGhQp7AVUfJWIBZp1K/ayBYHFy56GwQb
Cabitg0fpqx9Pv6EcRHeTZwJyhXdEjiPZMX0ikPYd3kCgYEA+tiJ7h4jute/WfRL
tfZvhsrrYYrnk5sYGsakR2SZAkbq9fLo3U1ZXKGoXQ3ZRKGiR8GrH1gzgT9XDpxR
RxqHa6gCYALqJuggMdCYJxWfAtJcBbpIing9CeT1Ki7cQzzGEhU9NYVKQYYieWWC
BfF3EaDJ2coJ/pXTWhMNklYP8x0CgYEAxD7KP1HNoXDbsQ0zDxbgAHEvtklGHTQW
7gybZoo+9F1LPJQQm2Z0G3ZrCps4sSrtHaTZK0XoQF9EKtBluiAhSXMGyL+yr58X
XwgSpMK6DJBgfE42ESQIyb+vfbQ3KKKafvH5/4B9wMJuNUWn+woHc46dDa/UHQUd
maHpF2qqQucCgYEA7WRcNHNlkP944eKmfBA6v6/uTqOsQS64Ay8WbVIw08zVs+ks
o7L97QI4WcgvZBorgAkyrzlDlP+infslmErs+d9IUCCyBBwNy9cDB4oYsAzwdaMz
34enDGQX+NHcNe2f7aEYCjyYZ6ZPnd+Iy6MW8iHepTPlfX/BQy9g2qqD8akCgYEA
wrojaW08g8M+25JjZcenAglN9K0Em5nCXve3g6oOCeBA9Z1eVTT2ZQG9+UpImNQl
cNLQgzXc3XMqaula57NWFFHFG5HMNqPARxX1mfN3NVxVwULCN4PwDHDeK/eU/AdN
EkX9cWAIaCsFvGqf4mPzPOD4Skp8SUd4NagJaKj4xWUCgYASC3cvdtHYgxfJk4m1
v3Fos2ATyJG7W/BywVDQD7wzoEYtalKpq5UGKoEACOy3YxbNPDgVUywvuKZZnpvQ
phfqMyC7ET8291Z7TbWPGywfSW+aORmiKQ0cW5wavKhVxQQnO/8K2aiEV8gBRi19
cIZbPkIielowJKxADN+CWFe4xw==
—–END PRIVATE KEY—–
Murad Hossain, today there is only one free decryptor, it is described in this article. This decryptor has the ability to decrypt files that were encrypted with the offline key. More details about the types of keys that the ransomware uses are described above.
I’ve got this as an error:
ID: 1Sx7Ha3LFcd1Bj1Yynhjn4MFnXPHCNCxX1wARbpW
What am I expecting in the future
helo boomfield,
how did u decrypt files using private key? can u tell us
i was infected with an toec and i used your decrypter but unsucssesfull.
waiting for your new decryptor sir .
Any idea when we will get a decryptor thatll work on online key encryption.
i tried to encrypt the leto files but it shows a error …..Unable to decrypt file with ID: 0180jYgs9f6sd7Zfr9HgEMM7trMd9JTrp4CKanSHtQnOl9BNfx3D
What’s the reason?…Please help
‘0180jYgs9f6sd7Zfr9HgEMM7trMd9JTrp4CKanSHtQnOl9BNfx3D’ id means the files were encrypted with an online key. Files encrypted with such a key cannot be decrypted, since the key is in the hands of criminals. I recommend trying the alternative methods listed here.
Unable to decrypt file with ID: ePf0IbjnNamulKcEVgjFfq14XvXvOAct85SZeiTd
0182Asd374y5iuhldeBYpv49WAKE19tduUzdsqESHLLtNkFpmbpG7OCmJ is my id and the decryption did not work. Please help