STOP Djvu Ransomware Decryptor is a free decryptor created by Emsisoft and Michael Gillespie that allows everyone to decrypt files that were encrypted with the STOP ransomware. Currently, this decryptor can decrypt most variants of this ransomware (148 variants). Part of other versions of this ransomware, namely, cases when encrypted files have the extension: .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, can be decrypted using STOP Puma decryptor. Unfortunately, in most cases, it is impossible to decrypt files that are encrypted with new versions of this ransomware (starting from August 2019). If you become a victim of one of these new variants, then at the moment you can only decrypt files that were encrypted with offline keys.
What is STOP Djvu Ransomware
STOP Djvu Ransomware is the most active and widespread ransomware. Like other ransomware, it is designed to encrypt files that can only be decrypted after payment of the ransom. According to the ID Ransomware, to date, more than 450,000 victims have already been discovered, and their number is increasing by approximately 1,500 people every day. The reason for this is that this ransomware is mainly distributed through adware, cracks, free programs and key generators, allowing users to activate paid software. Children, students and many other users, are looking for freeware, download and run it, not knowing that in this way they can allow the ransomware to penetrate on the computer.
Summary
| Name | STOP (Djvu) ransomware |
| Type | Crypto virus, Filecoder, Crypto malware, File locker, Ransomware |
| Encryption algorithm | The ransomware encrypts files using a strong encryption algorithm, which is called Salsa20. |
| Encrypted files extension | .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .djvut .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad, .promorad2, .kroput, .kroput1, .charck, .pulsar1, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .forasom, .berost, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, ,vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, prandel, .zatrov, .masok, .brusaf, londec, .krusop, .mtogas, .coharos, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .stare, .cetori, .carote, .shariz, .gero, .hese, .geno, .xoza, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .noos, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, .kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt, .cdmx , .cdqw |
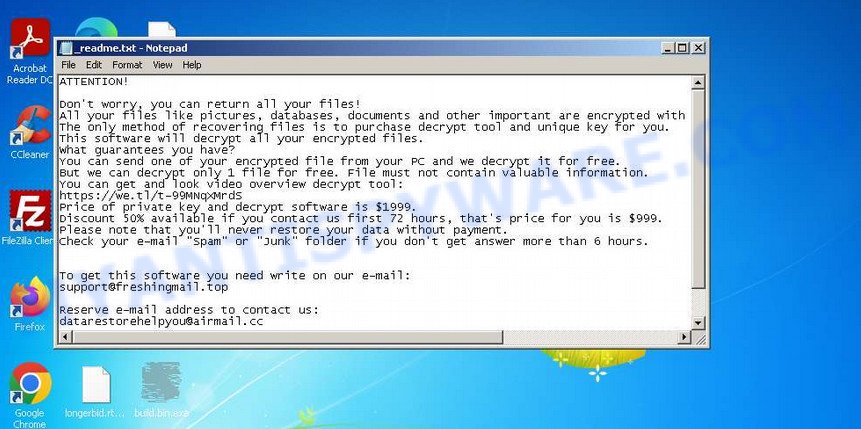
| Ransom note | In each directory where the ransomware encrypted the files, it drops a new file (ransom demand message). The very first versions of STOP used the following file names: !!!YourDataRestore!!!.txt, !!!RestoreProcess!!!.txt, !!!INFO_RESTORE!!!.txt, !!RESTORE!!!.txt, !!!!RESTORE_FILES!!!.txt, !!!DATA_RESTORE!!!.txt, !!!RESTORE_DATA!!!.txt, !!!KEYPASS_DECRYPTION_INFO!!!.txt, !!!WHY_MY_FILES_NOT_OPEN!!!.txt, !!!SAVE_FILES_INFO!!!.txt and !readme.txt. Starting with the version that, after encryption, added the .djvu * extension, the ransom note had the following file name: _openme.txt, _open_.txt or _readme.txt. The most recent versions of the STOP Djvu Ransomware use only one file name: _readme.txt. |
| Contacts | STOP ransomware developers often change the email addresses that are used to contact victims, the last of them are listed below: support@freshingmail.top, datarestorehelp@airmail.cc, support@bestyourmail.ch, admin@helpdata.top, manager@time2mail.ch, supportsys@airmail.cc, support@sysmail.ch, helprestoremanager@airmail.cc, manager@mailtemp.ch, supporthelp@airmail.cc, helpteam@mail.ch, restoremanager@airmail.cc, restoreadmin@firemail.cc, restoremanager@firemail.cc, helpdatarestore@firemail.cc, helpmanager@mail.ch, helpmanager@firemail.cc , helpmanager@iran.ir, helprestore@firemail.cc, datarestore@iran.ir, datarestorehelp@firemail.cc, datahelp@iran.ir, restorealldata@firemail.cc, restorefiles@firemail.cc, restoredatahelp@firemail.cc, salesrestoresoftware@firemail.cc, salesrestoresoftware@gmail.com, gorentos@bitmessage.ch |
| Ransom amount | $1999, $999 (if paid within 72 hours) |
| Encryption keys | Security researchers have determined that STOP Djvu Ransomware uses two types of encryption keys. The first one is online keys, the ransomware uses these keys if during encryption it has access to the network and can connect to its command-and-control server. These keys are unique to each computer. The second group is offline keys. The ransomware uses these keys if it does not have a connection to its command-and-control server. These keys are the same for different computers. That is, the same key can be used to decrypt files regardless of which computer they were encrypted on. To date, security researchers have found offline keys for some variants of STOP Djvu Ransomware. |
How to decrypt files encrypted by STOP Djvu Ransomware
Depending on the version of STOP Djvu Ransomware, you need to perform different steps to decrypt files. The version of STOP Djvu can be determined by the extension of the encrypted files. Before decrypting files, you need to be 100% sure that the ransomware is completely removed. We recommend that you use several tools (with different anti-virus engines) to scan your computer and remove STOP Ransomware and other malware. Some of the best and free malware removal tools are listed in this article – Best Free Malware Removal Tools.
1. Old STOP ransomware
A variant of STOP ransomware using the extension: .puma, .pumas, .pumax. All known variants of this ransomware can be decrypted using STOP Puma decryptor. Also, with this decryptor, in some cases, files with the following extension can be decrypted: .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT.
Download the decryptor from the link below
https://www.emsisoft.com/ransomware-decryption-tools/stop-puma
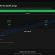
Right-click on the downloaded file (decrypt_STOPPuma.exe) and select “Run as Administartor”. You will be shown the license terms, click yes to continue. The program starts, you will see a window, as in the example below.
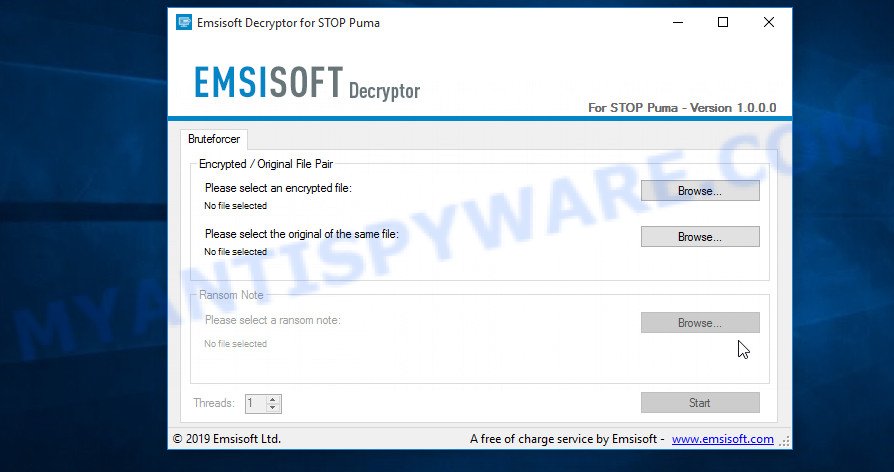
STOP Puma decryptor
As we already reported above, in order to use this decryptor you need one, or better, several pairs of files, one of which is encrypted, and the other is its original version. Having prepared the corresponding pairs, then you need to select them using the corresponding buttons in the program window. When ready, press the Start button. As soon as the key is found, the decryptor will immediately inform you. In some cases, an error may occur while searching for a key, therefore we recommend using several pairs of files to be sure that the correct key has been found.
After the correct key is found, you will be able to decrypt the files. Select the location where the encrypted files are located and click the Decrypt button.
2. STOP Djvu ransomware
A variant of the STOP Djvu ransomware using the extension: .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote.
In order to decrypt files you need to find several pairs of files. Each pair of files consists of an encrypted file and its original copy. File size over 150kb. After you find several pairs of files, do the following. Open the following link in a new window.
https://decrypter.emsisoft.com/submit/stopdjvu/
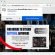
You will see a page called STOP Djvu Decryption. An example of this page is given below.
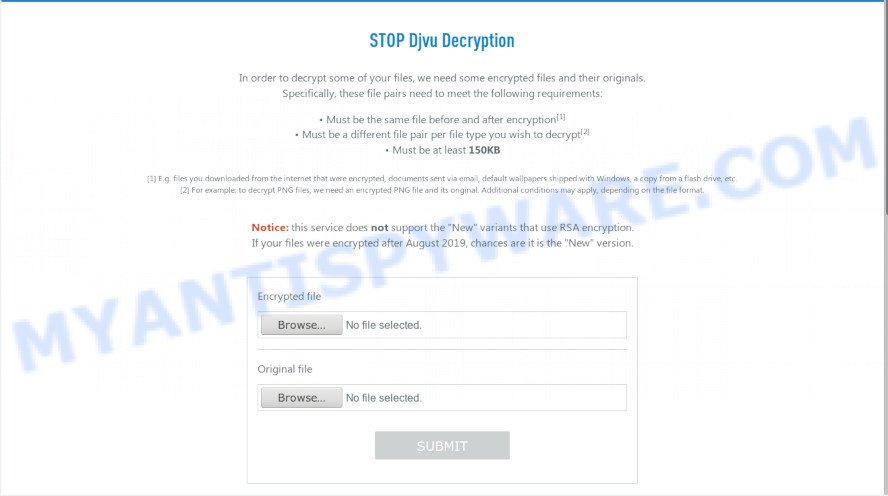
STOP Djvu Decryption
On this page using the Browse button, enter the path to the encrypted file and its original copy, then click the Submit button. After clicking on the Submit button, your files will be uploaded to the server. Then the key search process starts. Please be patient, this process may take some time. As soon as the key is found, an appropriate message will appear on the page and you will be asked to download the decryptor.
Click on the link called “Click here to download the decryptor“. The page from which you can download the decryptor will load. Click the Download button and save the decrypt_STOPDjvu.exe file to your computer.
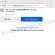
When the file is downloaded, start it by right-clicking on it and selecting item “Run as Administrator”. When it starts, the Windows can show you UAC Promt, then click Yes. After that, you will be shown the license terms and a small instruction, please read this information to continue.
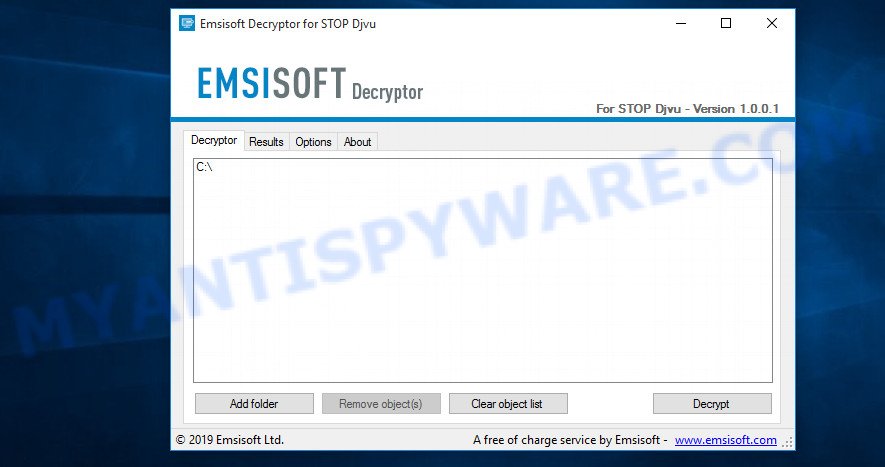
STOP Djvu decryptor
In the main window, select the disk or directory where the encrypted files are located, and then click Decrypt. After that, the decryptor will begin to decrypt the files for which the key was found at the previous stage. If the decryptor skips files, saying that it cannot decrypt them, then you need to again find a couple of files, one of which is encrypted, and the second is its original copy. Then use them to find the decryption key.
3. New Djvu ransomware
The latest version of STOP Djvu ransomware uses the following file extensions: .coharos, .shariz, .gero, .hese, .geno, .xoza, .seto, peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, gcyi, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt. An updated variant of this version appears every few days, the main difference between all variants is the extension of encrypted files. The last variant encrypts files with the .qqmt extension; the personal ID of the victims of this variant starts with 0540.
At the moment, it is possible to decrypt files only in some cases when they are encrypted using an offline key. To decrypt files, download the decryptor using the following link.
https://www.emsisoft.com/ransomware-decryption-tools/stop-djvu
Click the Download button and save the decrypt_STOPDjvu.exe file to your computer. Right click to it and select ‘Run as Administrator’. Confirm permission to run the program by pressing the Yes button. Read the license terms and brief instructions. In the main window that opens, select the disk or folder where the encrypted files are located and click the Decrypt button. If the decryptor skips files without decrypting them, then the offline key for them is unknown or they are encrypted with an online key.
This video step-by-step guide will demonstrate How to decrypt files locked by STOP Djvu ransomware.
Finish words
We hope that the set of utilities and services developed by Emsisoft and Michael Gillespie helped you decrypt all the files. If the decryption of the files failed, then do not forget that there is another way to recover your files – is to use data recovery tools. Details on how to recover encrypted files without a key and decryptor are described in the article:
How To Recover Encrypted Files (Ransomware file recovery).











The extension name of my file is .qpss, is it fixable?
First try the EmsiSoft decryptor, if it fails to decrypt encrypted files, then try ShadowExplorer and PhotoRec (How to recover encrypted files). If these free tools did not help to recover encrypted files, then you just have to wait for the moment when decryption becomes possible. Follow the news on our website.
File: D:\Encrypted\IMG_20171104_110623.jpg.mado
Error: No key for New Variant online ID: inz7FAcm2NdFNpn7O0YckNXDvbzm2T5kdw143cpt
Notice: this ID appears to be an online ID, decryption is impossible
The “inz7FAcm2NdFNpn7O0YckNXDvbzm2T5kdw143cpt” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hey Please held me.
My files were encrypted with online ID and the extension of all the files is .dehd
Mid ID is 0369UIhfSddyT5GT9WC7qH80KijHYxcdhhigu4977uChIDezfE
The “0369UIhfSddyT5GT9WC7qH80KijHYxcdhhigu4977uChIDezfE” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ayuda uidg no ha salido ayuda
Hi! I appreciate your work immensely and it helped me in several situations, but unfortunately after about 2 years, I found a virus almost identical to the CERBER Virus, I believe you already heard about it but just by the name DEJvu, they encrypted my files and as you mentioned having knowledge they require around 980$ for ransom. THE EXTENSIONS THEY USED FOR ENCRYPTION ARE: EGFG / XCVF. THANKS ANYONE WHO CAN HELP ME WITH THIS.
First try the EmsiSoft decryptor, if it fails to decrypt encrypted files, then try ShadowExplorer and PhotoRec (How to recover encrypted files). If these free tools did not help to recover encrypted files, then you just have to wait for the moment when decryption becomes possible. Follow the news on our website.
Pessoal me ajuda, meus arquivos ta tudo criptografado. tem mais de 700 GB bloqueado pelo esse mal MALDITO. eu tenhos ARQUIVOS DE 10 ANOS ATRAZ CRIPETOGRAFADO, FOTAS, VIDEOS, DOCS ETC. eu to muito triste.
Meu ID= 0458JIjdmBCNMNe5hCnY9b2AAjwpoGVWQ15RZRAoRXdXzmMm5
The “0458JIjdmBCNMNe5hCnY9b2AAjwpoGVWQ15RZRAoRXdXzmMm5” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
File: C:\Program Files\Steinberg\Vstplugins\Reveal Sound\Factory Presets\Synth\SY Zodiac Synth V.spf2.jhgn
Error: No key for New Variant offline ID: u8l8S1WNPrtypqzE5TnCErdyo7HLDDCUTJi8Vbt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Archivo: C:\Archivos de programa\Steinberg\Vstplugins\Reveal Sound\Factory Presets\Synth\SY Zodiac Synth V.spf2.jhgn
Error: no hay clave para la nueva variante ID sin conexión: u8l8S1WNPrtypqzE5TnCErdyo7HLDDCUTJi8Vbt1
Aviso: esta identificación parece ser una identificación fuera de línea, el descifrado PUEDE ser posible en el futuro
Your files are encrypted with an offline key. Therefore, first try the EmsiSoft decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec (How to recover encrypted files). If these free tools did not help to recover encrypted files, then you just have to wait for the moment when decryption becomes possible. Follow the news on our website.
0477JIjdmX79CQK8jIC0qZYL7eTrXBqlus2b7fVpoE3McgRFZ this is my id
The “0477JIjdmX79CQK8jIC0qZYL7eTrXBqlus2b7fVpoE3McgRFZ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
0229yiuduy6S5dgxkfMsZThIw4DwBHZc8ybx6mfASOUWMOkEYiCLBa
MY ID got affect Nlah virus
The “0229yiuduy6S5dgxkfMsZThIw4DwBHZc8ybx6mfASOUWMOkEYiCLBa” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
0483JIjdmXITW8OzNKjHfRBroA20SDNyO32QJSP2ce2j8hAzk this is my id
The “0483JIjdmXITW8OzNKjHfRBroA20SDNyO32QJSP2ce2j8hAzk ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
0472JIjdmy7HghPpzPon4nGWrnLRmMMXgfh010dXbl6ESYIgt
The “0472JIjdmy7HghPpzPon4nGWrnLRmMMXgfh010dXbl6ESYIgt ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
All the files of my external hard drive is corrupted with .nnuz
it is possible to have access again to all the files with this method ?
My computer is not corrupted, just this external hard drive
try PhotoRec as demonstrated in the following article: https://www.myantispyware.com/2019/12/04/how-to-recover-encrypted-files-ransomware-file-recovery/
Emsisoft decrypt_stopdjvu has stopped working
please help me my pc cant open file it ransomware FDCV pls help me
my pc got effected by ransomware and all files has extention of .ZFDV
i did a complete format of my system .
but i saved some effected files which i need to decrypt
please suggest
THANK YOU
hi
my files corrupted with kruu virus
please remove and recover my files
Use the following guide: https://www.myantispyware.com/2022/05/12/how-to-remove-kruu-ransomware-decrypt-kruu-files/
– RETOUR D’EXPERIENCE ! –
Bonjour,
Ayant été infecté en Août 2021 (par téléchargement d’un logiciel) du ransomware STOP/DJVU avec l’extension .guer , et après avoir tout tenté pour récupérer mes fichiers avec les outils et décryptors Emsisoft proposés ici (mais impossible), je me suis résout à finalement contacté les pirates 8 mois plus tard (la mort dans l’âme).
Attention, je n’encourage personne à payer la rançon !
Mais ceci est mon retour d’expérience, pour témoigner de ce qu’il s’est passé pour moi.
Après un premier échange de mail 4 mois après l’attaque, pour en savoir plus sur le processus de paiement, et après une flambée du bitcoin, je les ai re-contacté par mail 4 encore après.
Et là surprise, leurs deux adresses mails n’étaient plus disponibles !
J’ai ainsi fais le tour des forum pour tenter de récupérer toutes les autres adresses correspondant à mon virus Guer.
Sur les 18 dénichés sur les forums (via les témoignages de victimes), seul 1 m’a répondu, en en profitant au passage pour augmenter le tarif de 0.013 à 0.022 BTC …
Au final, j’ai accepter (je voulais récupérer ces données qui étaient importantes pour moi) et j’ai payer les 0.022 BTC via LocalBictoins.
Et, après une relance par mail dans la journée au pirate, celui-ci m’a bien donné le décrpteur et la clé privée pour que je puisse déchiffrer toutes mes données (environ 2 To quand même …).
Encore une fois, je n’encourage personne à le faire, mais il est important de savoir que les pirates ont bien joué le jeu dans mon cas.
En espérant que cela pourra être utile 🙂
Do you have any solution of .bnrs files ? Will you refer any .bnrs files decryptor? TIA
Use the following guide: https://www.myantispyware.com/2022/06/06/how-to-remove-bnrs-ransomware-decrypt-bnrs-files/
How to decrypt qlln
Use the following guide: https://www.myantispyware.com/2022/05/24/how-to-remove-qlln-ransomware-decrypt-qlln-files/
my files become : *.LLTT
How to fix this, plz ?
My files become: *.LLTT
0504JhyjdVtEct4mZjVQfO6TrbndVyvg4GlWQPGK61nyMB9uS
How to fix this, plz ?
The “0504JhyjdVtEct4mZjVQfO6TrbndVyvg4GlWQPGK61nyMB9uS ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
KcZEKULAGlHqW6qeUCECqfgoYtUCDAAw3dj7sDO7
this id online or offline?
The “KcZEKULAGlHqW6qeUCECqfgoYtUCDAAw3dj7sDO7 ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Please help me recover my files here is my online id 0262ergaVFFZ0QJwtRMxdkGJHhgPLszSnA0t6szZea2wTAYt
The “0262ergaVFFZ0QJwtRMxdkGJHhgPLszSnA0t6szZea2wTAYt ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
please ooxa decrypt
my files become : *.qqkk
Use the following guide: https://www.myantispyware.com/2022/08/27/how-to-remove-qqkk-ransomware-decrypt-qqkk-files/
Buenas!!!!
alguien me podria ayudar.
Archivos infectados con QQKK
personal ID:
0549Jhyjd0y6Uxb2u6j8CbtEYbWdh1r9eRvr5m8ZHrZH3aM9L
0556JhyjdD0vvdy7DQLaBINw6ws0IWL2wqhaWNgFqVy2s4UZV
you need to add the file extension (EEMV), I recently got ransomware and that was the extension being used
Hi sir,
Is it possible to decrypt qqlc virus with online key, I have planning to keep the files and is it possible to decrypt it in the future?
of course, there is a chance that decryption will become possible in the future, but when is unknown
is the following id decryptable? 0417Jsfkjn76iiUSiI78xDFQtmmOLObCQBIBBswUEaeGW4p4va
The “The “0417Jsfkjn76iiUSiI78xDFQtmmOLObCQBIBBswUEaeGW4p4va ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.