Have you ever received an email that begins with Greetings, I am sorry, but I have to start with the bad news, claiming extensive access to your accounts and devices, and even threatening to release compromising videos and browser history to your contacts? Don’t be alarmed—it’s a scam.
These scammers use intimidation tactics, such as claiming they have installed tracking software on your devices and accessed your personal email and webcam. They demand a ransom, often in Bitcoin, and set a tight deadline to create urgency. This kind of email is a classic example of a sextortion phishing scam.
We’re here to clarify that these threats are typically baseless and designed to exploit your fear. For a detailed explanation of this scam and effective strategies to deal with it, read our comprehensive article. Stay aware and safeguard yourself from these deceptive practices.
Here’s an example of the “I am sorry, but I have to start with the bad news” email:
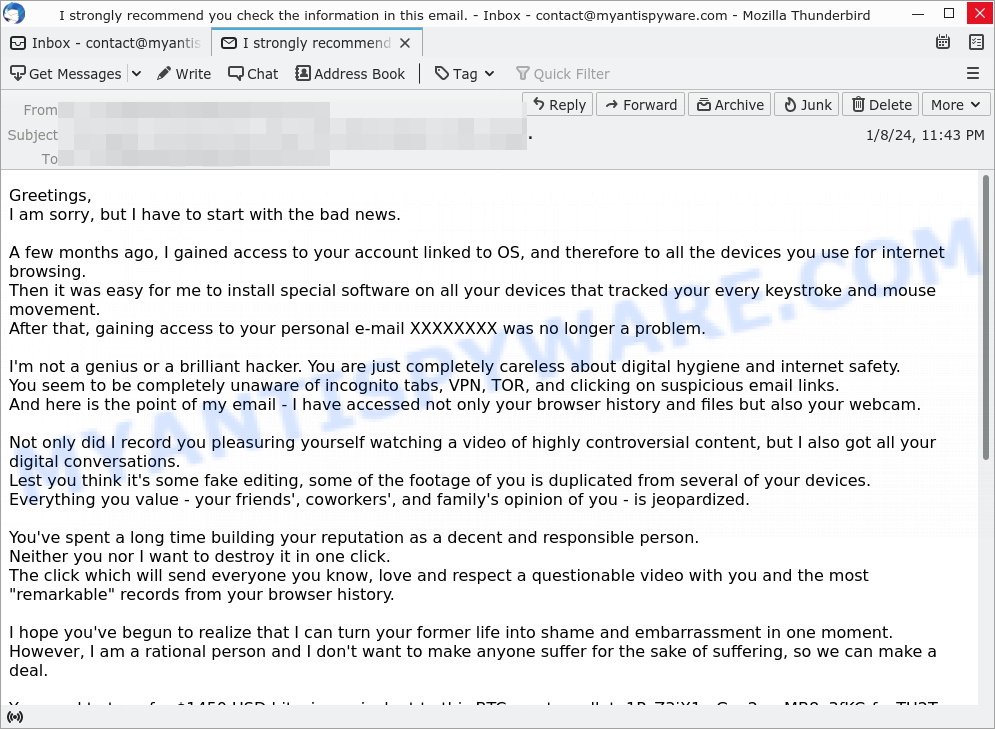
Table of Contents
Is this a scam email?
YES, this email, which asserts that the sender has hacked your devices, accessed your email and webcam, and threatens to release compromising material, is undoubtedly a scam. It’s a typical sextortion phishing attempt, aiming to instill panic and urgency.
The scammer uses intimidation tactics, claiming to have installed tracking software and recorded you, to seem credible. They exploit fears of personal and reputational damage, demanding a ransom in Bitcoin for the supposed deletion of this material. However, these claims are almost always baseless, designed to manipulate you into paying money unnecessarily.
Red Flags That Indicate a Scam:
- 📧 Claim of Hacked Account and Devices: The scammer’s assertion that they have gained access to your devices and accounts is a major red flag. This claim is meant to instill fear and create a sense of urgency, but it is often baseless.
- 🔐 Threat of Releasing Compromising Material: The threat to release compromising videos and browser history is designed to provoke immediate anxiety and shame. However, this is a common scare tactic, and in most cases, the scammer has no such material.
- 💸 Demand for Payment in Bitcoin: Requesting a ransom in Bitcoin highlights the scammer’s intention to remain untraceable. The use of cryptocurrency for payment is a typical sign of a scam, as it’s difficult to trace and recover once paid.
- ⏰ Time-Sensitive Ultimatum: Setting a strict deadline, such as a 48-hour window for payment, is a tactic to pressure you into acting quickly and without rational thought. This urgency is a hallmark of scam emails.
- 🚫 Warnings Against Contacting Authorities: The scammer’s warning against contacting police or changing security settings is a tactic to prevent you from seeking help and to maintain control over the situation.
In short, the ‘Greetings, I am sorry, but I have to start with the bad news’ email is a scam. The scammer uses intimidation tactics and false claims to instill fear and coerce you into paying a ransom. Do not engage or send any money. Instead, delete the email, update your passwords, enable two-factor authentication where possible, and consider reporting the incident to your email provider and the relevant cyber crime authorities. Staying informed and vigilant is your best defense against these deceitful practices.
How the scam works
When an email lands in your inbox, flashing a password you recognize and loaded with threats, it’s like an alarm bell going off 🚨. You’re immediately hit with the question: “How did they get my email and password?” This is a classic tactic in cyber scams, often using details harvested from data breaches found on the darker corners of the internet 🔍.
The email typically throws around vague threats, hinting at releasing personal videos or information 🎥. This ambiguous wording is designed to create doubt and fear: “Could this be a real threat?”
Next, the scammer claims they’ve installed a malware on your devices, supposedly giving them full access to your data 💻. But here’s a red flag – they offer no proof 🚩. It’s a textbook scam move: use fear, not facts, to intimidate.
This leads to the critical moment: the ransom demand 💰. They’ll want a swift Bitcoin payment, knowing it’s difficult to trace and recover. They’re exploiting the fear factor, rushing you into a decision. However, paying up provides no assurance they’ll actually delete the supposed data. It might even mark you as an easy target for future scams.
As the email unfolds, you might question, “Is my data truly at risk?” or “Can the scammer be tracked down?” 🕵️♂️ In most cases, these threats are empty, more about leveraging your fears than actual cyber intrusion.
So, what’s the next move? Engaging with the scammer or fulfilling their demands isn’t the way to go. Instead, beef up your digital defenses: update your passwords, run a thorough antivirus scan, and consider alerting the authorities if personal data like a password is involved 🔐. This situation underscores the need for robust cybersecurity measures and constant vigilance in the digital landscape.
The email read as follows:
Greetings,
I am sorry, but I have to start with the bad news.A few months ago, I gained access to your account linked to OS, and therefore to all the devices you use for internet browsing.
Then it was easy for me to install special software on all your devices that tracked your every keystroke and mouse movement.
After that, gaining access to your personal e-mail XXXXXXXX was no longer a problem.I’m not a genius or a brilliant hacker. You are just completely careless about digital hygiene and internet safety.
You seem to be completely unaware of incognito tabs, VPN, TOR, and clicking on suspicious email links.
And here is the point of my email – I have accessed not only your browser history and files but also your webcam.Not only did I record you pleasuring yourself watching a video of highly controversial content, but I also got all your digital conversations.
Lest you think it’s some fake editing, some of the footage of you is duplicated from several of your devices.
Everything you value – your friends’, coworkers’, and family’s opinion of you – is jeopardized.You’ve spent a long time building your reputation as a decent and responsible person.
Neither you nor I want to destroy it in one click.
The click which will send everyone you know, love and respect a questionable video with you and the most “remarkable” records from your browser history.I hope you’ve begun to realize that I can turn your former life into shame and embarrassment in one moment.
However, I am a rational person and I don’t want to make anyone suffer for the sake of suffering, so we can make a deal.You need to transfer $1450 USD bitcoin equivalent to this BTC crypto wallet: 1PzZ3jX1zrGov2qyrMB8x3fKCrfxvTU2Tx
It’s a very small amount for not losing the reputation you’ve been developing for years, maybe even decades.
Once I receive payment, I will delete all materials once and for all.
Since I monitor all your PC and mobile activity, I’ll notice when you send the payment as well as when you read this email.
You have 48 hours to make a payment, starting from the moment you open this e-mail.I’m a man of my word, you can trust me, otherwise, I would have published it long time ago. Some advice in advance:
– Don’t reply to this letter. This email was sent from a randomly generated address.
– Don’t call the police or any other authorities. As soon as I notice you’re trying to contact them,
the videos will be published online. In addition to that, crypto wallets are anonymous, so no one will ever track me.
– Don’t try to reinstall your system or reset your device. As I mentioned, as soon as I get a notification of such activity, I will post all the materials.I’m sorry that we had to meet under such circumstances, but fate is fate.
Adios, senor. I hope this is the last time we interact.P.S. Kind reminder: please be more careful about your internet security from now on, and then you will never run into such situations.
All in all, this scam uses tricks to make you scared and rushed. If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
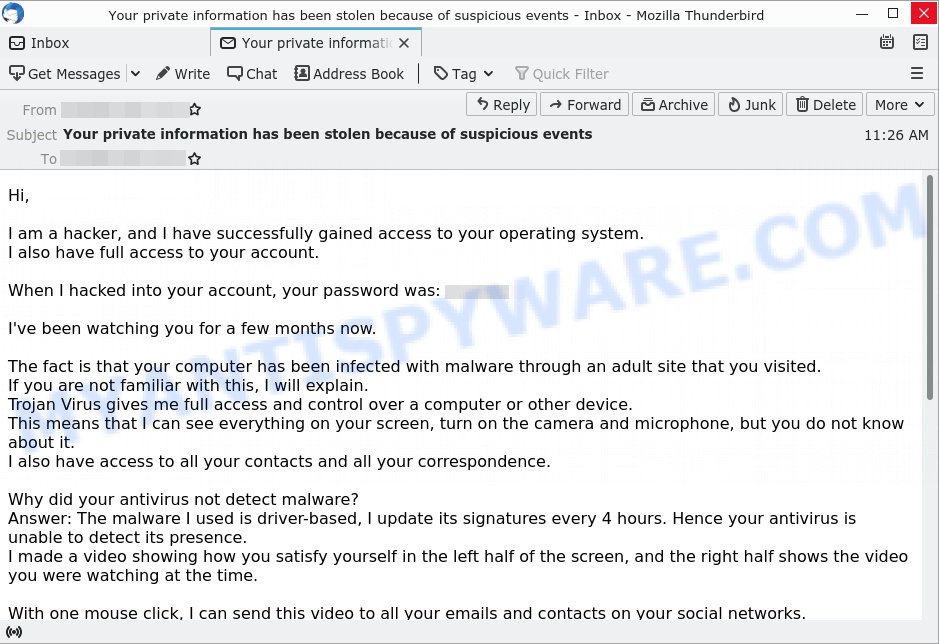
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
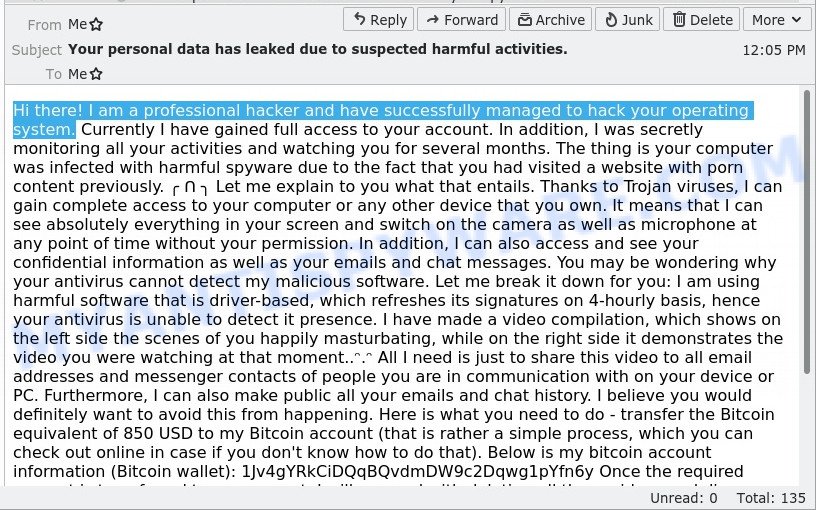
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
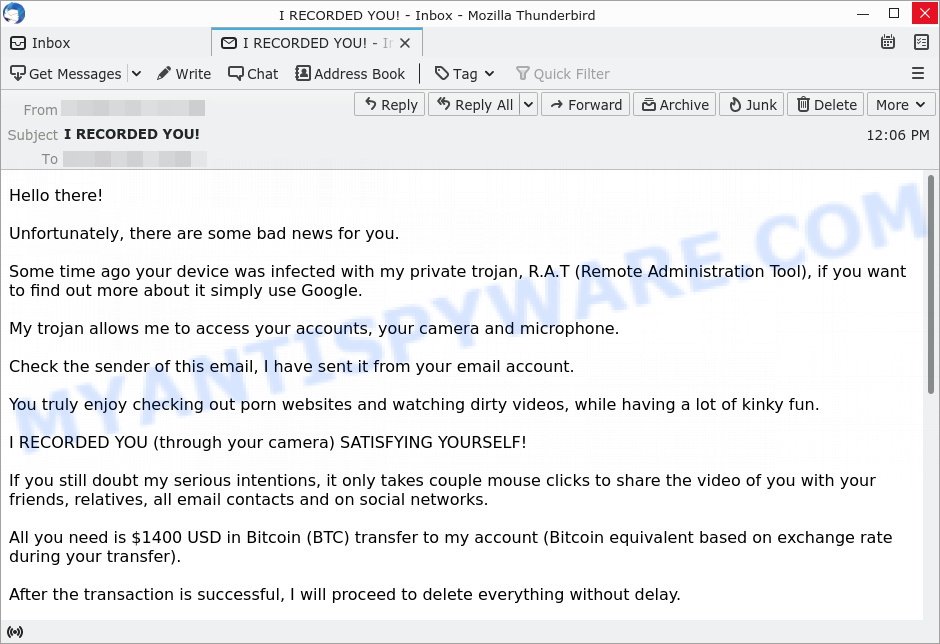
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “I am sorry, but I have to start with the bad news” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | Greetings, I am sorry, but I have to start with the bad news. |
| Type | Phishing/Sextortion |
| Email Subject | I strongly recommend you check the information in this email. |
| Ransom amount | $1450 USD (in Bitcoin equivalent) |
| Bitcoin Address | 1SmBDTt7nd3654t9Dstbmd4YiF3qCNEaF, 1PzZ3jX1zrGov2qyrMB8x3fKCrfxvTU2Tx |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The ‘I am sorry, but I have to start with the bad news’ email scam shows how cybercriminals try to scare people into giving them money. They do things like pretending to send emails from your own address and making big claims without any real proof. The best way to deal with these scams is to understand how they work. Always be careful online, don’t make quick decisions based on these emails, and focus on keeping your information safe.