If you’ve been experiencing unexpected browser redirects, you might be wondering: “What is a virus that redirects web pages?” You’re not alone. Many users experience this issue, often caused by malware that alters browser behavior. Let’s delve into the reasons behind these redirects and how you can resolve them.
Table of Contents
🌐 Browser Redirects: Common Causes
Browser redirects can disrupt your online experience by unexpectedly taking you to different websites. To effectively tackle this issue, it’s crucial to first identify the underlying causes. In the following discussion, we outline all the possible factors that can lead to browser redirects, from viruses specifically designed for this purpose to incorrect configuration settings. Understanding these causes is the key step in resolving such redirects, ensuring a more secure and seamless browsing experience.
1. Browser Hijacker 🦠
This form of malware stealthily modifies browser settings, pushing users to certain web pages, mostly for malicious intents. Often, they can change your homepage, default search engine, or inject pop-up ads.
2. Adware 📢
Annoying yet pervasive, adware is software that automatically displays or downloads advertising material. When browsing, you might encounter unexpected pop-ups or even be redirected to promotional pages or potentially harmful sites.
3. Rogue Browser Extensions 🔌
Extensions can enhance the browser’s functionality, but rogue ones can have the opposite effect. They might redirect you to commercial or malicious websites, often without any indication of their activities.
4. Infected System Files 💾
If malware manages to infect critical system files, it could lead to unpredictable browser behavior, including unwarranted redirects.
5. Manipulated DNS Settings 🔄
Sometimes, the DNS (Domain Name System) settings on your device are tampered with, causing your web requests to be routed to different servers, leading to unexpected destinations.
6. Compromised Router 📡
Rarely, but importantly, cybercriminals can hack into routers, changing DNS settings to redirect web traffic through malicious servers.
7. Session Hijacking 🚫
In this type of attack, unauthorized users can capture or intercept a user’s session to take over or manipulate their web sessions, which could lead to redirections.
8. Websites with Redirect Scripts 🔀
It’s worth noting that some legitimate websites employ redirection scripts for various reasons, such as tracking user behavior, affiliate marketing, or serving regional content. However, they can be misused for sinister purposes.
🕵️♂️ Why Do Cybercriminals Use Redirect Viruses?
Redirect viruses, while a nuisance to users, offer multiple advantages to cybercriminals. Delving into their motives can provide better insight into the threats lurking online and how to protect against them.

1. Monetary Gain 💰
For many cybercriminals, it’s all about the money. By pushing users to specific pages, they can amass significant ad revenue or affiliate commissions. Each redirect, click, or interaction could put coins in their virtual pockets.
2. Phishing Attacks 🎣
Redirection often leads unsuspecting users to fake sites, replicas of legitimate ones. Here, users might unwittingly enter personal details, login credentials, or even financial information, handing it straight to the criminals.
3. Malware Distribution 🦠
The end destination of a redirect isn’t always just a website; it could be a trap. Cybercriminals use these redirected sites as platforms to host and spread additional malware, compounding the user’s security issues.
4. Data Harvesting 📊
Beyond immediate gains, some redirect viruses are designed to surveil. They track browsing habits, gather demographic information, and even record keystrokes, amassing data that can be sold or used for targeted scams.
5. Expanding Botnets 🌐
Some sophisticated redirect viruses aim to recruit the infected device into a botnet, a network of compromised devices. These botnets can be employed for various malicious purposes, from DDoS attacks to further spreading malware.
6. Reputation Damage 🚫
For some, the intent isn’t profit but sabotage. By redirecting users from legitimate websites to malicious or scandalous ones, they can tarnish the reputation of organizations or individuals.
7. Cryptocurrency Mining ⛏️
Redirecting users to sites that secretly utilize the user’s computing power to mine cryptocurrency has become a growing trend. This cryptojacking approach offers a financial reward for the perpetrators without direct theft.
🛠️ How to remove browser redirects
If you’re facing unwanted browser redirects, this section will guide you on how to get rid of them. We’ll show you step by step how to check for and delete any viruses that cause redirects. You’ll also learn how to change your browser settings and remove any malicious extensions that might be causing these redirects. Our instructions are easy to follow, aimed at helping you solve this problem quickly and effectively. By the end of this guide, you should be able to browse the internet without any unwanted interruptions.
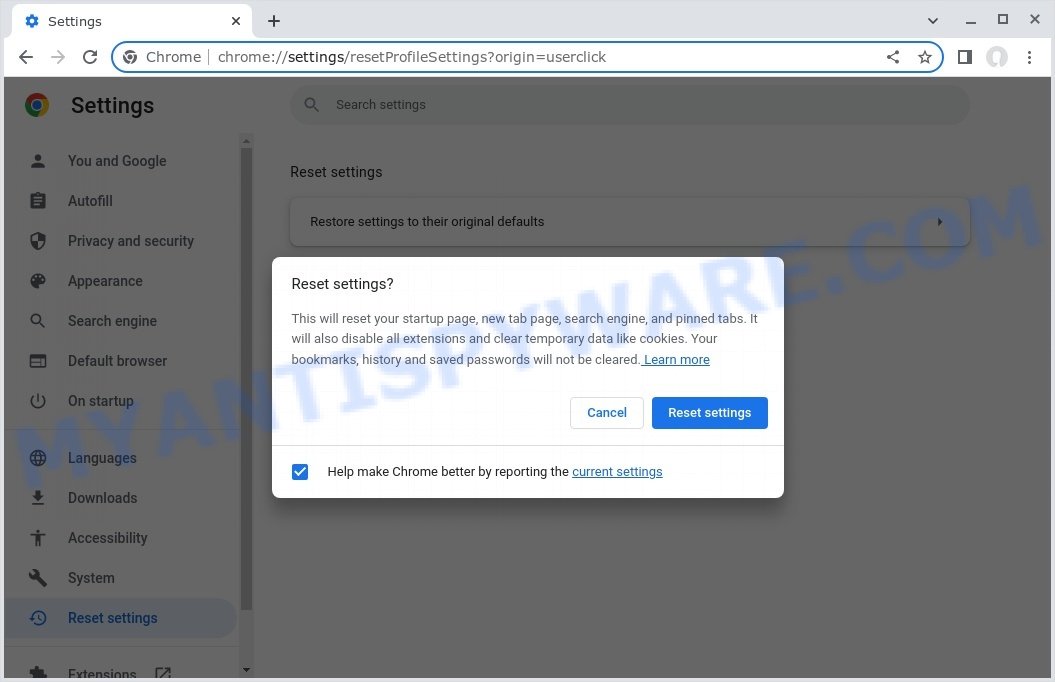
Uninstall Suspicious Programs 🗑️🖥️
Browser redirects often originate from malicious software inadvertently installed on your system. To tackle this, start by reviewing the programs currently installed on your computer. Prioritize removing any unfamiliar applications, especially those recently added or that appear questionable. Be cautious, as undesirable software can sometimes be masked within legitimate installations.
|
|
|
|
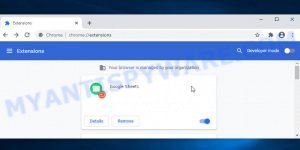
Check Installed Extensions 🔌
Understanding which extensions are installed in your browser is crucial to ensure your online security. Malicious or compromised extensions can often be the root of unexpected behavior like browser redirects. Here’s a step-by-step guide for checking installed extensions in different browsers, presented in table format:
|
|
|
|
Scan with Antivirus Software 🦠🚫
Use a reputable antivirus or antimalware program to scan your computer. Ensure it’s updated with the latest definitions for maximum efficacy. MalwareBytes is a trusted anti-malware tool with a strong track record. It’s been widely recognized for its efficiency in detecting and eliminating a broad range of threats, from sneaky browser extensions to more aggressive forms of malware. By employing advanced scanning techniques, MalwareBytes digs deep into your system, ensuring no malicious elements go unnoticed. Simply download, install, and run a full scan with MalwareBytes to clear out any lingering threats related to the Searchparrot.world or other potential risks.
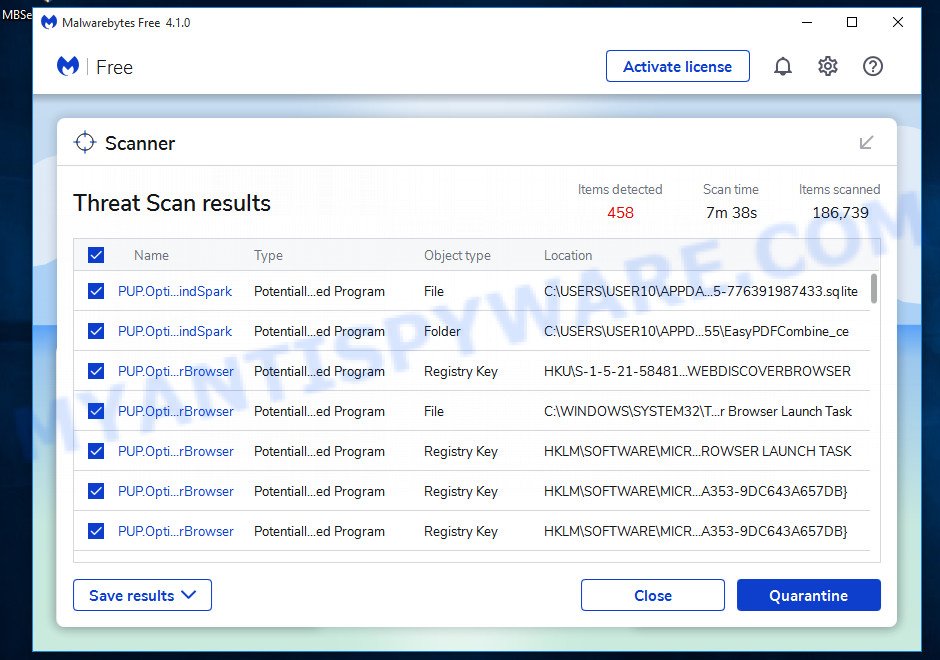
- Download Malwarebytes by clicking on the link below. Save it on your Windows desktop.
Malwarebytes Anti-malware
327098 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- Once the download is done, close all applications and windows on your personal computer. Open a folder in which you saved it. Double-click on the icon that’s named MBsetup.
- Choose “Personal computer” option and press Install button. Follow the prompts.
- Once installation is finished, scan your computer. Run a full scan of your computer to detect and remove any browser hijackers and other forms of malware. The scan may take several minutes to complete, depending on the size of your hard drive and the speed of your computer.
- Remove detected threats. If the scan finds any threats, click Quarantine to remove them. The software will automatically remove the browser hijacker and any associated malware. After the removal process is complete, restart your computer to ensure that any changes made by the hijacker are fully removed.
The following video demonstrates how to remove hijackers, adware and other malware with MalwareBytes.
Reset Browser Settings to Default 🔄
If you suspect that your browser settings have been tampered with, consider resetting them to their default state. Most browsers provide this option in their settings or preferences section.
|
|
|
|
Clear Browser Cache and Cookies 🍪🗑️
Old or corrupted cache and cookies might lead to unusual browser behavior. Clearing them might help resolve some redirection issues.
|
|
|
|
Review DNS Settings 🔀
Check if your DNS settings have been altered. Ensure you’re using trusted DNS servers, such as those provided by your ISP or well-known alternatives like Google’s 8.8.8.8.
|
|
Update Your Software 🔄📲
Outdated software can be more susceptible to malware attacks. Regularly update your operating system, browsers, and other software.
|
|
System Restore ⏪
If you’ve recently started experiencing browser redirects, consider restoring your system to a point before the problems began. This can often undo any malicious changes.
|
|
Router Checkup 📡
Ensuring your router’s security is crucial as it serves as the gateway to all your connected devices. An infected or compromised router can be the source of various online threats, including unwanted browser redirects. Follow the steps below for a basic router checkup:
- Login to Router Settings: Most routers can be accessed via a web browser by entering their IP address (commonly
192.168.1.1or192.168.0.1). You’ll be prompted to enter a username and password. If you haven’t changed these details, the default login credentials are often ‘admin’ for both fields, but it’s essential to check your router’s manual or the manufacturer’s website. - Change Default Credentials: If you’re still using the default login credentials, it’s crucial to change them. Cybercriminals often target routers with default settings.
- Update Router Firmware: Manufacturers release firmware updates to fix vulnerabilities and improve performance. Check for available updates and apply them. This option is typically found in the ‘System’ or ‘Update’ section of your router’s settings.
- Check Connected Devices: Review the list of devices connected to your network. If you notice any unfamiliar devices, it’s a sign your network might have been breached. Consider disconnecting unknown devices and changing your Wi-Fi password.
- Enable WPA3 Security: Ensure your Wi-Fi is protected with WPA3, the latest security standard. If your router doesn’t support WPA3, at least ensure it’s using WPA2. Avoid WEP as it’s outdated and easily hackable.
- Turn Off Remote Management: Remote management allows you to access your router’s interface from outside your home network. While it might be convenient, it also poses a security risk. It’s best to disable this feature unless you have a specific need.
- Regularly Restart Your Router: Occasionally restarting your router can help clear potential malware from memory. While it’s not a definitive solution, it’s a good preventive measure.
- Consider a Factory Reset: If you suspect your router is severely compromised, doing a factory reset can help. Remember, this will erase all your custom settings, so ensure you have backup configurations or note down essential details.
Seek Expert Assistance 👩💻🆘
If you’ve tried the above steps and the issue persists, it might be time to seek help. Consider reaching out to IT professionals or Myantispyware forums that specialize in malware removal and troubleshooting.
🛡️ Prevention Tips
By following these steps, you’ll reduce the risk of encountering redirect viruses and other online threats, ensuring a safer browsing experience.
- 🔒 Always Update Your Software: Ensure all your operating systems, applications, and especially web browsers are up-to-date. Cybercriminals often exploit known vulnerabilities in outdated software.
- 🌐 Use Caution When Clicking on Links: Avoid clicking on suspicious links, especially in emails from unknown senders. This is a common way for malware and redirect viruses to spread.
- 🔎 Install a Reliable Antivirus and Anti-Malware: Use trusted security software to detect and block potential threats. Regularly run scans to ensure your system remains clean.
- 🛍️ Download Wisely: Only download software and apps from reputable sources or official app stores. Third-party sites can host malicious software that looks legitimate.
- 🔥 Enable Firewall: Ensure your device’s firewall is active. This acts as a barrier between your computer and potentially harmful data on the internet.
- 🌍 Use a VPN: A Virtual Private Network (VPN) encrypts your online traffic, making it harder for cybercriminals to intercept or tamper with your data.
- 🧠 Educate Yourself: Stay informed about the latest cybersecurity threats and how to recognize them. Awareness is one of the best defenses against cyber threats.
- 🔑 Use Strong, Unique Passwords: Don’t reuse passwords across multiple sites. Use a password manager if necessary to keep track of your passwords.
- ⛔ Block Pop-ups: Enable pop-up blockers in your browsers. Some pop-ups can contain malicious scripts.
- 💡 Regular Backups: Always back up important data. If something goes wrong, having a backup means you won’t lose your important files.
Conclusion
In this guide, ‘What is a Virus that Redirects Web Pages?’, we’ve covered everything you need to know about browser redirects. From understanding their common causes to exploring why cybercriminals use redirect viruses, we’ve provided comprehensive insights. We also explained how to remove browser redirects, giving you practical steps to fix this issue.
The section on prevention tips is especially important, offering strategies to protect yourself from future incidents. Remember, being proactive about your online security is as important as knowing how to react when problems arise.
We hope this guide has been helpful in making your online experience safer and more enjoyable. Stay informed and cautious, and you can greatly reduce the risk of facing unwanted redirects while browsing.