Recover Encrypted Files is a question, the answer to which is important for all victims of ransomware attack. Ransomware is malicious software that encrypts files and demands a ransom for their release. Encrypted files cannot be opened, that is, all encrypted files are locked and cannot be used. This may result in loss of data or important information. Since ransomware uses a complex encryption algorithm, in most cases it is impossible to decrypt encrypted files manually or create a decryptor. But not everything is so bad, everyone who has become a victim of ransomware has a chance to recover encrypted files. In this article, we will show alternative ways to recover ransomware encrypted files. Each of the methods does not require the use of paid software, is easy to repeat, contains explanatory illustrations.
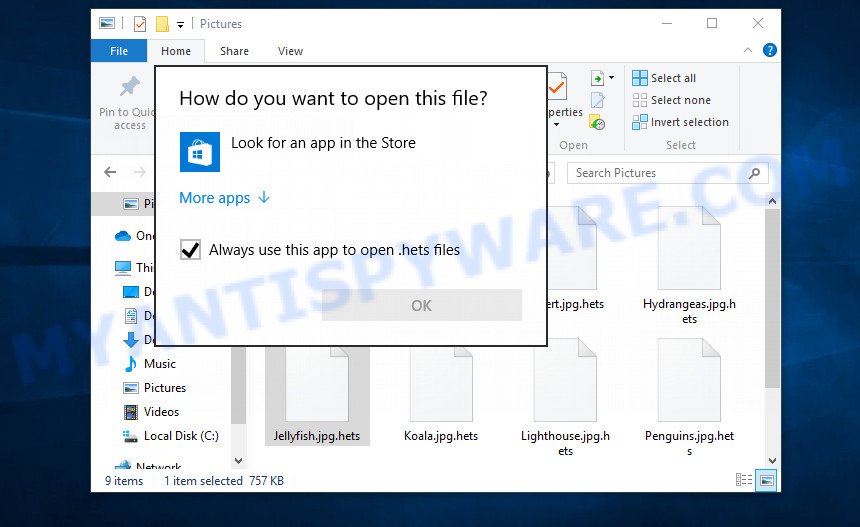
Encrypted files cannot be opened
Files encrypted by ransomware become useless, they cannot be used, their contents cannot be read. Even if you change the filename of the encrypted file, try to open this file in the editor, this will not help. In any case, Windows OS will report that the file was damaged or it is of an unknown type. To return files back, that is, to access their contents, encrypted files must be decrypted. Decryption requires a decryptor and a key. Ransomware authors offer victims to buy a key and a decryptor from them. Usually the size of the ransom is from 300 to 1000 dollars. All security experts agree that the ransom should not be paid. There is no guarantee that paying a ransom will provide a key to decrypt the encrypted files.

Although decrypting files requires a decryptor and a key, which are in the hands of criminals, this does not mean that ransomware victims have no hope of recovering encrypted files. This is not true! There is a chance that allows everyone to recover the contents of encrypted files. Depending on the type of ransomware, this chance may be greater or lesser. Unfortunately, there are very few methods to recover encrypted files without the help of the decryptor. Each of these methods requires neither a decryptor nor a key, therefore these methods are suitable for any victim and can help restore files after any type of ransomware.

Regardless of which method you choose, before you begin the process of recovering encrypted files, you need to check your computer for malware. You need to be sure that ransomware is no longer on the computer. Even if there are no signs of ransomware activity, this does not mean that it disappeared or deleted itself after all the files were encrypted. Ransomware probably just hides itself, and after the appearance of new unencrypted files on the computer, it activates again and encrypts these files. In addition, an active ransomware can be a source of infection for other devices, as well as work as a spyware, that is, collect various information about the victim, which will then be sold or transmitted to attackers.

We highly recommend that before you start recovering encrypted files, first check your computer for malware. It is very important to find the ransomware and completely remove it. In order to quickly find all parts of the ransomware and easily remove them, we recommend that you use free malware removal tools. Each of them tested by security experts, has a powerful malware detector, and will allow you to remove various types of malware, including ransomware, spyware, worms and trojans.
How to recover ransomware encrypted files
Recover encrypted files from Volume shadow copies
Volume shadow copy is a feature on modern versions of Microsoft Windows (Vista,7,8,10). It is turned on by default and creates copies of all user files. These copies can be created automatically from time to time or when creating a restore point. This allows you to retrieve copies of files that have been encrypted by ransomware. To access these shadow copies, we recommend using a program called ShadowExplorer. It is a free program that does not require installation, has a simple interface and is easy to use.
Download ShadowExplorer on your computer by clicking on the link below.
439489 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
When the file download is complete, open the directory in which you saved the file. Right click to ‘ShadowExplorer-0.9-portable’ and select ‘Extract all’. You will see a window, as in the following figure.
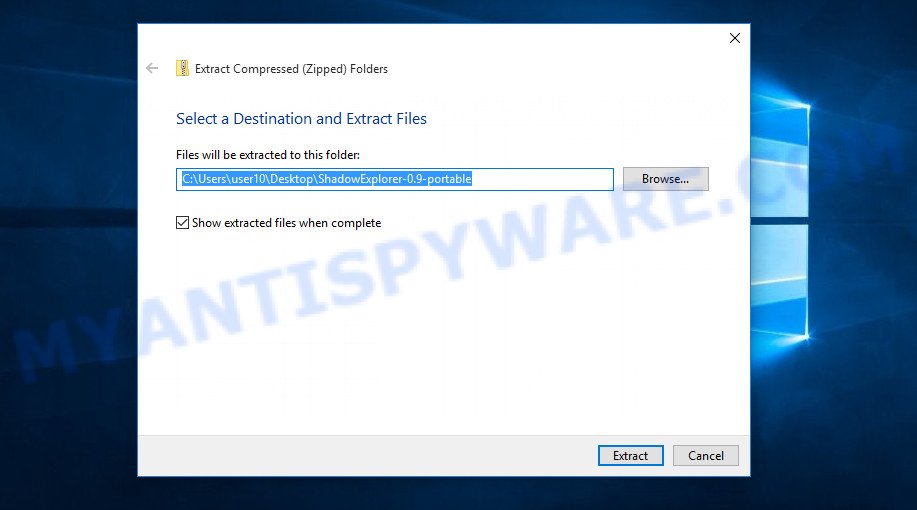
Here you can change the place where the archive will be unpacked. If you do not make any changes, then in the directory where the file is located, a directory with the name ‘ShadowExplorer-0.9-portable’ will be created in which all the unzipped files will be placed. Then the contents of this directory will open. Now open directory ‘ShadowExplorerPortable-0.9’. The following is an example of the contents of this directory.
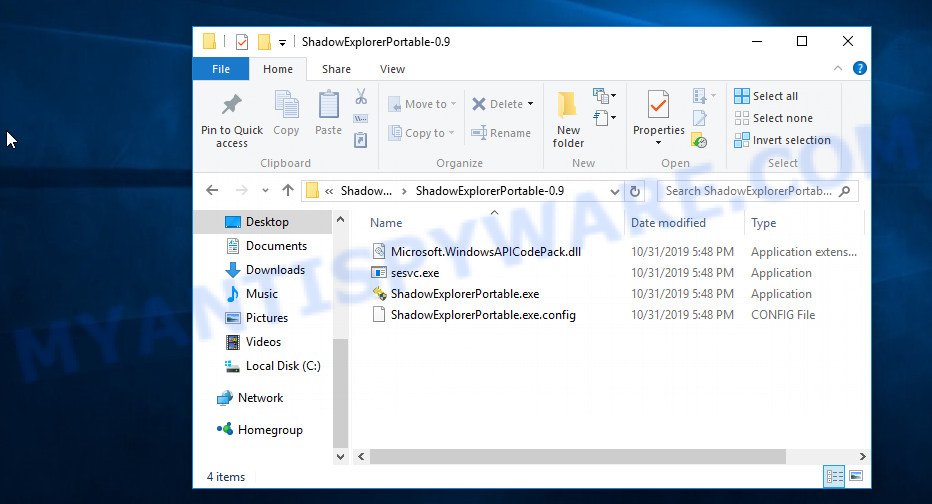
Find the ShadowExplorerPortable file and run it. You will see the main window of ShadowExplorer similar to what is shown in the picture below.
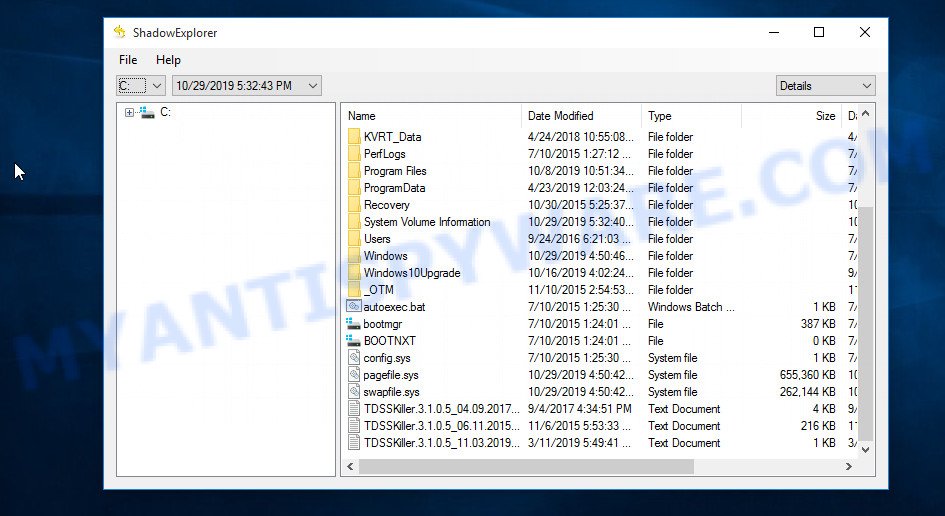
In the upper left corner of the window, select the drive on which encrypted files are located that you want to recover. Then, slightly to the right of the drive name, select the recovery point that is before the moment the files were encrypted.
On right panel look for a file that you wish to recover, right click to it and select Export as shown on the image below.
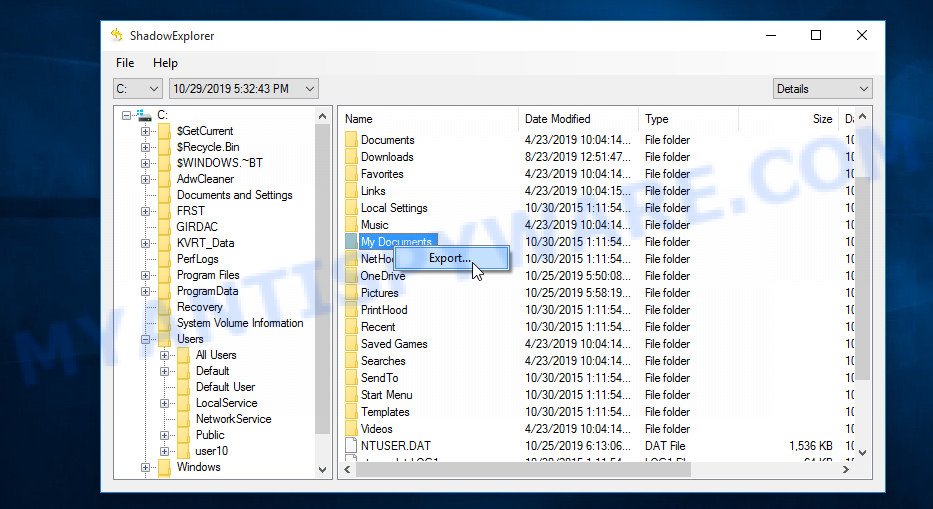
Now select the directory where the recovered files will be saved, then click OK button.
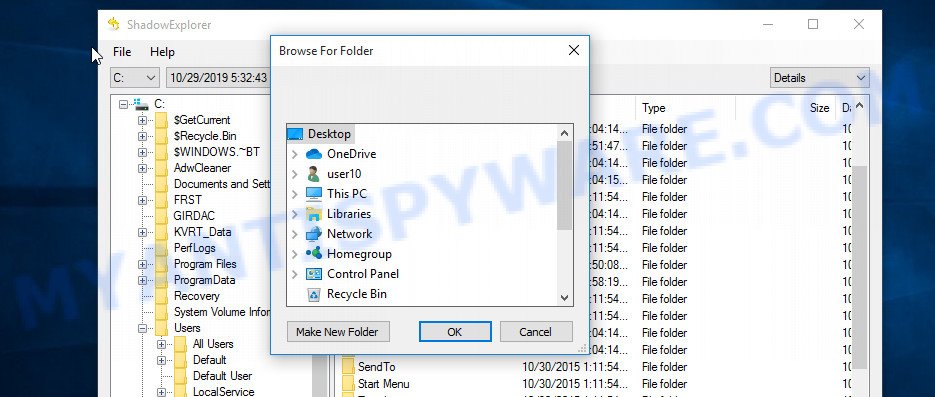
Unfortunately, ransomware often deletes all Shadow copies, and this blocks the ability to use the method described above to recover encrypted files. Therefore, if ShadowExplorer did not find Shadow copies (the field in which the recovery points are listed is empty), then all Shadow copies have been deleted. In this case, you have only one option left, to use data recovery tools. This method of recovering encrypted files is described below.
This video tutorial will demonstrate how to Recover encrypted files from Volume shadow copies using Shadow Explorer.
Recover encrypted files using Photo Rec
Data Recovery Utilities is your last chance to recover encrypted files. Why data recovery tools can help recover encrypted files? Before encrypting the file, some types of ransomware copies its contents to the computer’s RAM, encrypts it, then deletes the non-encrypted file, and writes the encrypted file to the hard disk. In reality, not-encrypted files are not physically deleted; they are simply marked by Windows OS as deleted. Data recovery software scan the computer’s hard drive for such files, and then restore them.
PhotoRec is a free data recovery tool that can help you recover encrypted files. This program has all the necessary functions and is absolutely free. In addition, PhotoRec has repeatedly proven its effectiveness. With its help, many users were able to recover the contents of encrypted files.
Download PhotoRec on your machine by clicking on the link below.
After the file download is completed, open the directory where you saved the file. Although PhotoRec does not require installation, but since it is delivered in the archive, you must unpack the archive before using it. Right click to testdisk-7.x.win and select Extract all. Follow the prompts. By default, the program will be unpacked into a new directory, which will be created in the directory where the downloaded file is located. When unpacking is completed, you will see a new directory with the name testdisk-7.x, open it.
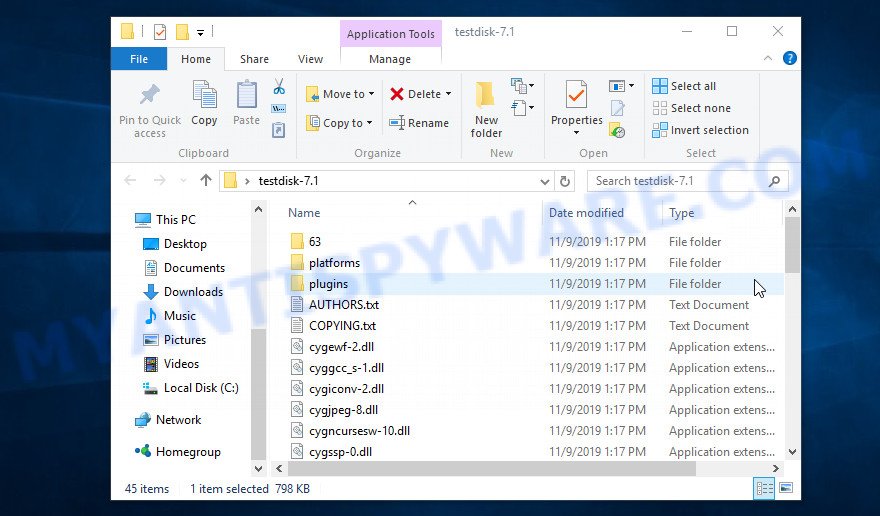
Scroll down the directory until you find a file named qphotorec_win. Run it. You will be shown the main program window as on the image below.
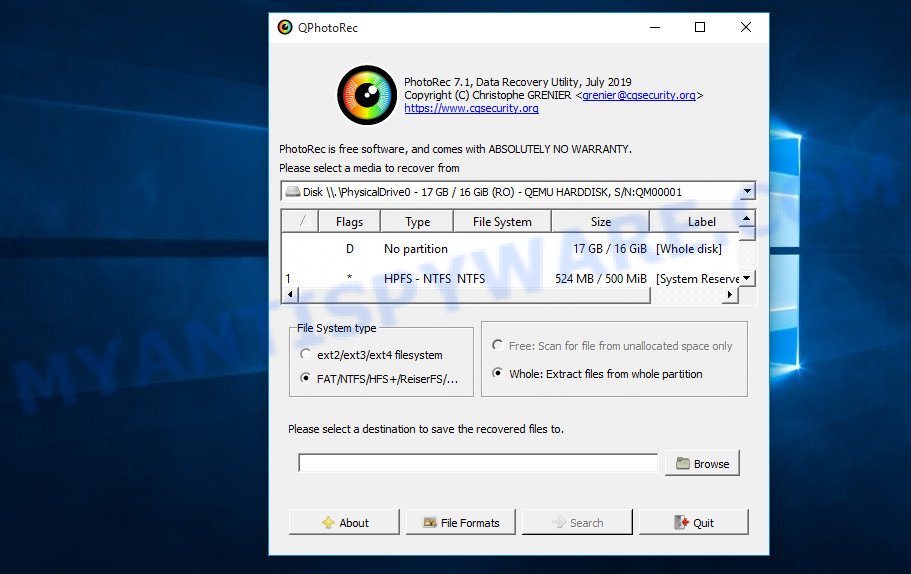
Find the box that is signed by “Please select a media to recover from”, right-click on it and select the device on which the encrypted files are located.
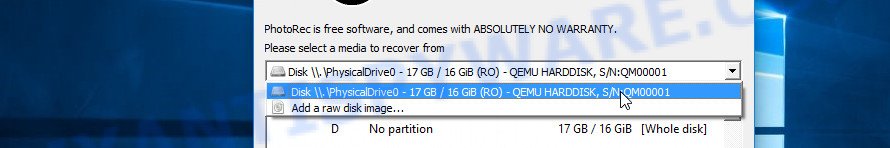
PhotoRec will scan the partition table of the selected device and show a list of partitions in the list. Select the partition from which you want to start the recovery of encrypted files. Be careful, pay attention to the type of partition (usually NTFS) and its size. Skip sections marked ‘System Reserved’.
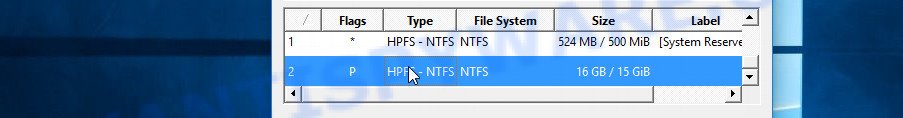
Having decided where PhotoRec will look for unencrypted files, now you need to select the types of files you want to restore. Click File Formats button, a small window opens with a list of file types that PhotoRec has the ability to find and restore. We advise you to leave only those types that you really need, so you will significantly speed up the process of searching and restoring files. After you make your choice, click the OK button.
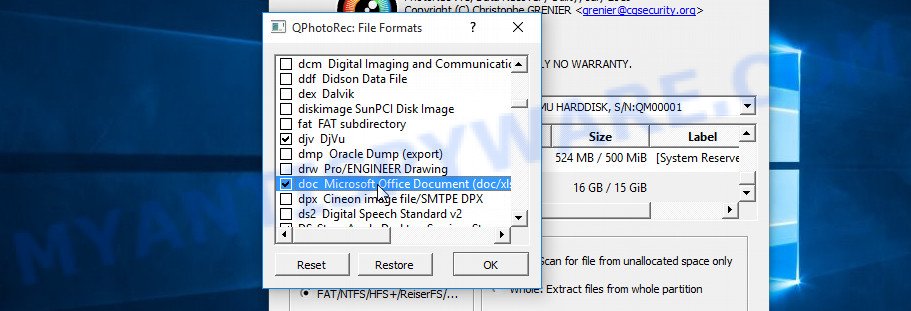
And lastly, click on the Browse button and select where the recovered files will be written. We highly recommend that you select an external drive, flash drive, or a separate section of the internal drive. If you restore files to the same disk on which you are looking for them, then the restored files will overwrite files that have not yet been found, which will block the ability to restore their contents.
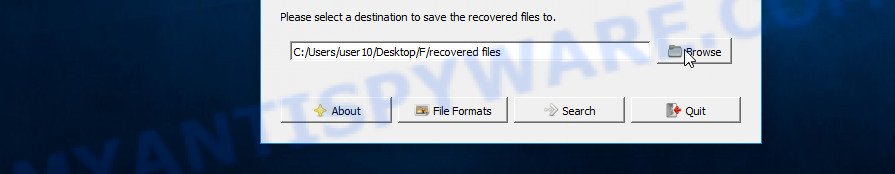
Now you can start file recovery. Just click the Search button. The program will start searching and restoring files. PhotoRec will open a window in which information on the count of recovered files will be updated in real time.
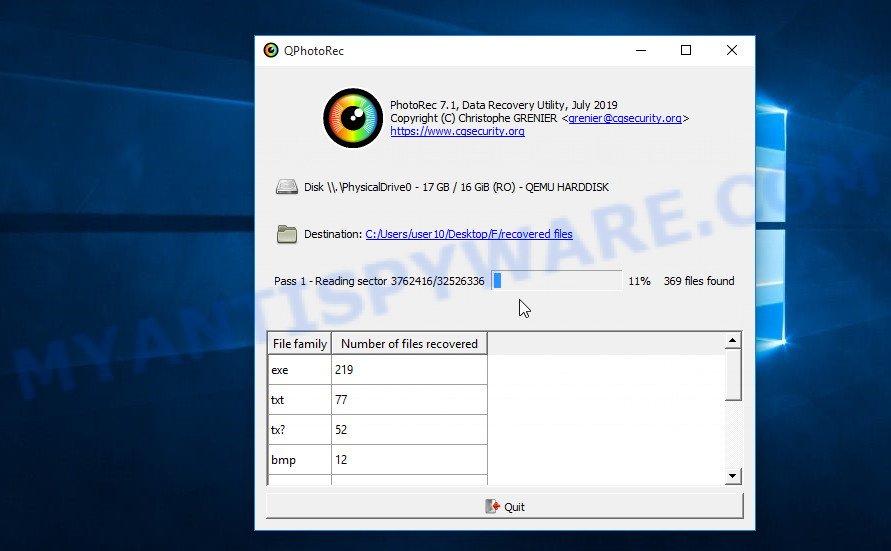
All files that were restored are written to the directory that you specified above. When the file recovery process is completed, press the Quit button. Open the directory where the recovered files were written. You will see something like the following.
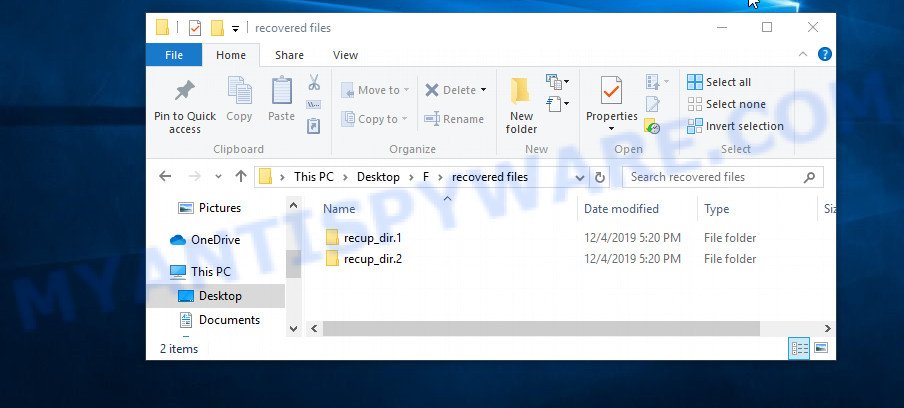
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your restored files by filename, extension and/or date/time.
This video tutorial will demonstrate how to Recover encrypted files using PhotoRec.
Finish words
This manual is designed to help ransomware victims recover encrypted files for free. If you have any questions or comments, then write to us. If you need help, please ask your question here.











thank you…!
Thank you for sharing your knowledge 🙂
thank you, but this one couldn’t help me though
Que tal. Consultas: el 14 de abril me infecte con .lalo ransomware. La pc me empezó a fallar además de encriptarme todo. Formatie el disco c (disco sólido) e instale windows 10 desde 0. Aparentemente quedo funcionando todo bien, hice escaneos con antyapiware e instale el norton 360. Me gustaria saber si al formatear el .lalo virus puede seguir vivo? Y por otro lado tenia 2 discos duros internos, uno de 1 tb y el otro de 2tb obviamente ambos discos quedaron con todos los archivos encriptados con .lalo. Lo que hice luego de probar con shadow explorer sin exito ya que no me permitia volver más atras del 14 de abril que fue el dia que fui infectado. Acto seguido desconecte estos 2 discos duros y ahora tengo miedo de conectarlos. Que hago los conectó y pruebo con photoRec o si los conectó puedo revivir el virus ya que aparentemente al formatear me quedó todo bien y me da miedo conectar los discos que estan infectados. Muchas gracias.
You can connect the disk to an uninfected computer, and then use the Photorec to try to recover the contents of the encrypted files. There is practically no danger of computer infection.
It doesn’t show me anything when I cross to Drive C,D,E
If ShadowExplorer does not show any files on these disks, then the shadow copies were deleted by the ransomware or the recovery service for these disks was disabled. However, you can try PhotoRec to recover files located on these disks.
My files are encrypted by online key sqpc ransomware so it didn’t decrypted by the emsisoft decrypt tool, but from shadow explorer file is converted without sqpc extension but it won’t open by the application or give the the could not open the file message, so what should I do in this situation to retrieve my file???
It is impossible to say exactly what is the reason that the restored file does not open, perhaps this file is damaged. Is this problem the same for all files recovered with ShadowExplorer?
how do i recover files and data corrupted by ransomware? all file types have been changed to lalo files,
i system restore doesnt help, ive tried file recovery programs but they just list the corrupt files after completing a scan.
i dont have any form of a backup – and cannot even access my outlook pst. file to be able to recover some documents via my emails..
pls can sme1 advise me what to do..
At the moment, there is no way to decrypt .lalo files, even if they are encrypted with an offline key, since the key has not yet been determined by security researchers. If the methods described above did not help you, then there are no other options. The only thing, in some cases, you can restore the contents of some encrypted files of larger sizes. For example zip archives, it is enough to remove the extension .lalo and then get the files from the archive.
hello, i want to ask about Photorec. do we have to recover all the disk or we can choose to scan only 1 disk? since it showed the list of the disk but i cant choose it, thanks
First you need to select a physical device, and then the partition on it.
Thanks a lot for this tool. But I could recover only some part of all of my data. Is there any way to recover all of it?
To date, there are no other ways than those described above.
“Photorec archieve is unknown or damaged”.. when u extract the file you get this error message
Clear your browser’s cache and download the Photorec file again.
Do you know if it id possible to recover deleted shadow copies?
Yes it is possible. But there is no easy way to do this.
Hello
The virus has deleted all the shadow copies ,
How can I recover the Deleted Shadow Copies ?
There is no easy way, but it is possible. To restore deleted Shadow copies, you can use vss_carver.py – https://github.com/mnrkbys/vss_carver
Do you have any guide how to install vss_carver. There is no clear guide to install the .py script + lib/shadow files. I would be able to work out the rest if i know how to get it running.
I have python installed and have tried multiple ways to get it to run to no avail.
Photo reci Kullandığımda pykw dosyasını göremiyorum Yardım Edin Dosyaları Göremiyorum
Muito obrigado, me salvou, quando vi o cronometro travei a maquina e eles não mandaram o pedido, só que todos meus arquivos já estavam com extensão .maas e nenhum programa descriptografava
PhotoRec was able to recover all my files infected with REPL. After the longest search for remedy, I can now finally end my worries. Thank you so much!
Dear Sir / Madam,
Accidentally My Computer is infected by .kuus ransomeware. All My Data Are Encrypted.
I Will be Very Grateful if You give idea or tool name to recover(decrypt) my data .kuus ransomeware. I have already formatted c: Drive, Data are in another drives and extra hdds.
Krishna
Today, .kuus files cannot be decrypted, even if they are encrypted with an offline key. But, if the files are encrypted with an offline key, then file decryption may become possible in the future. Despite the fact that you formatted the disks, there is a small chance that you will be able to recover some files with the help of PhotoRec.
Thank you one million times is not enough for your great work and valuable information
I’ve removed the virus and recovered almost all my files
Thank you infinity of times
Very Thank you for sharing your knowledge
I have been infected by .kook virus is there any possible way to decrypt my files I have removed the virus from my laptop pls help.
Today there is no way to decrypt .kook files. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files. If your files are encrypted with an offline key, then perhaps in the future, when the security researchers obtain the key, decryption will become possible.
are these tools above remove encrypted files kind of zida?
is this work to .geno files?
yes
Hi, good day. I have a question. I saved my Vari infected files on my external hard drive, since I have decided to reformat my laptop from that ransomware. Hoping there’s a chance to recover some of it. can photorec decrypt or restore my encrypted files made by vari? and will it affect my newly reformatted laptop if I connect my external hard drive that has my encrypted files? and do I need to connect my internet while running photorec? thank you advance.
yes, you can use PhotoRec even if you reinstall the Windows OS. This tool does not require an internet connection, so you can simply write PhotoRec to a USB flash drive and run from it.
my files our damage by kasp ransomware i cannot decrypt it using your tool because it is online most of my files are video and adobe premiere project files i cannot open it now here is my id 0249Oowhu342uw4egBGFxqKzjqJ3Ai5q3JJ0xfQ1sg3byk3TrAS
if your files are encrypted with an online key, then these files cannot be decrypted, since only the authors of the ransomware have the key. The only way to recover files is to use ShadowExplorer and PhotoRec.
My Computer has been infected by .boop virus. How can i descrypt .boop files? My system image backup also has been deleted. What can i do? Please help me.
Try PhotoRec
Hey mr
I used photorec and it recovered 40% of my files , i would like know why ? I know my ID is an online key so i cant decrypt it and it looks like i cant use shadow files because the ransomware just deleted it 🙁 Im looking for recovering that shadow files but i wonder if you have a tutorial or some guide to do that
Unfortunately, today there are no other ways to recover encrypted files other than those described in this article. Subscribe to our channel, as soon as the file decryption appears, we will inform all our subscribers about it.
oh god, i got same problem like saiko, now i’m stressed. my pc attacked by KOLZ virus, and the encrypt is online, can u please help me mr ?
Use the following guide: https://www.myantispyware.com/2020/09/20/remove-kolz-ransomware-decrypt-kolz-files-kolz-file-recovery/
HOLA… tengo un problema con el ramsomware de extencion .efji eh buscado toda la informacion accesible en internet y aun no encuentro solucion esto me paso el 18/10/2020
I have reset my pc when the attack happened since I was in pretty big trouble and didn’t had time to browse, now it’s showing it was online key. Is there any ways?
if the files are encrypted with an online key, it is impossible to decrypt them, since only the authors of the virus have the decryption key. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Help, please! My files are encrypted with .sglh ransomware, online key. I managed to clean my computer from the ransomware, but my files are still encrypted. what should I do? Desperately need help ….
if the files are encrypted with an online key, it is impossible to decrypt them, since only the authors of the virus have the decryption key. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Thank you so much for this helpful article ! I got my files (Shadow copies) but most of them are corrupted so i cant open them D: Is there a way to fix the corrupted files 🙁
Try PhotoRec
Bonjour, mon ordinateur est infecté par le ransomeware .lisp. Toutes mes données sont cryptées.
Je serai très reconnaissant si vous donnez une idée ou un nom d’outil pour récupérer (décrypter) mes données .lisp ransomeware. Merci beaucoup
Use the following guide: https://www.myantispyware.com/2020/11/24/how-to-remove-lisp-ransomware-decrypt-lisp-files/