Recover Encrypted Files is a question, the answer to which is important for all victims of ransomware attack. Ransomware is malicious software that encrypts files and demands a ransom for their release. Encrypted files cannot be opened, that is, all encrypted files are locked and cannot be used. This may result in loss of data or important information. Since ransomware uses a complex encryption algorithm, in most cases it is impossible to decrypt encrypted files manually or create a decryptor. But not everything is so bad, everyone who has become a victim of ransomware has a chance to recover encrypted files. In this article, we will show alternative ways to recover ransomware encrypted files. Each of the methods does not require the use of paid software, is easy to repeat, contains explanatory illustrations.
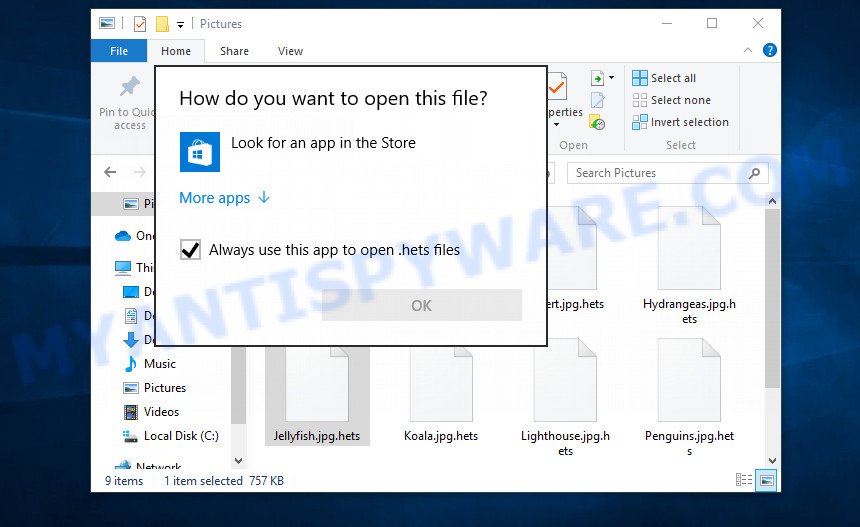
Encrypted files cannot be opened
Files encrypted by ransomware become useless, they cannot be used, their contents cannot be read. Even if you change the filename of the encrypted file, try to open this file in the editor, this will not help. In any case, Windows OS will report that the file was damaged or it is of an unknown type. To return files back, that is, to access their contents, encrypted files must be decrypted. Decryption requires a decryptor and a key. Ransomware authors offer victims to buy a key and a decryptor from them. Usually the size of the ransom is from 300 to 1000 dollars. All security experts agree that the ransom should not be paid. There is no guarantee that paying a ransom will provide a key to decrypt the encrypted files.

Although decrypting files requires a decryptor and a key, which are in the hands of criminals, this does not mean that ransomware victims have no hope of recovering encrypted files. This is not true! There is a chance that allows everyone to recover the contents of encrypted files. Depending on the type of ransomware, this chance may be greater or lesser. Unfortunately, there are very few methods to recover encrypted files without the help of the decryptor. Each of these methods requires neither a decryptor nor a key, therefore these methods are suitable for any victim and can help restore files after any type of ransomware.

Regardless of which method you choose, before you begin the process of recovering encrypted files, you need to check your computer for malware. You need to be sure that ransomware is no longer on the computer. Even if there are no signs of ransomware activity, this does not mean that it disappeared or deleted itself after all the files were encrypted. Ransomware probably just hides itself, and after the appearance of new unencrypted files on the computer, it activates again and encrypts these files. In addition, an active ransomware can be a source of infection for other devices, as well as work as a spyware, that is, collect various information about the victim, which will then be sold or transmitted to attackers.

We highly recommend that before you start recovering encrypted files, first check your computer for malware. It is very important to find the ransomware and completely remove it. In order to quickly find all parts of the ransomware and easily remove them, we recommend that you use free malware removal tools. Each of them tested by security experts, has a powerful malware detector, and will allow you to remove various types of malware, including ransomware, spyware, worms and trojans.
How to recover ransomware encrypted files
Recover encrypted files from Volume shadow copies
Volume shadow copy is a feature on modern versions of Microsoft Windows (Vista,7,8,10). It is turned on by default and creates copies of all user files. These copies can be created automatically from time to time or when creating a restore point. This allows you to retrieve copies of files that have been encrypted by ransomware. To access these shadow copies, we recommend using a program called ShadowExplorer. It is a free program that does not require installation, has a simple interface and is easy to use.
Download ShadowExplorer on your computer by clicking on the link below.
439489 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
When the file download is complete, open the directory in which you saved the file. Right click to ‘ShadowExplorer-0.9-portable’ and select ‘Extract all’. You will see a window, as in the following figure.
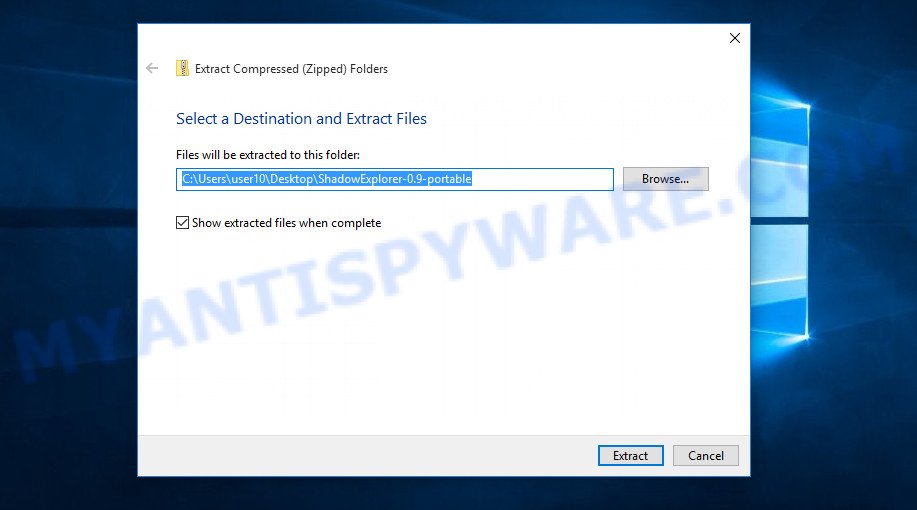
Here you can change the place where the archive will be unpacked. If you do not make any changes, then in the directory where the file is located, a directory with the name ‘ShadowExplorer-0.9-portable’ will be created in which all the unzipped files will be placed. Then the contents of this directory will open. Now open directory ‘ShadowExplorerPortable-0.9’. The following is an example of the contents of this directory.
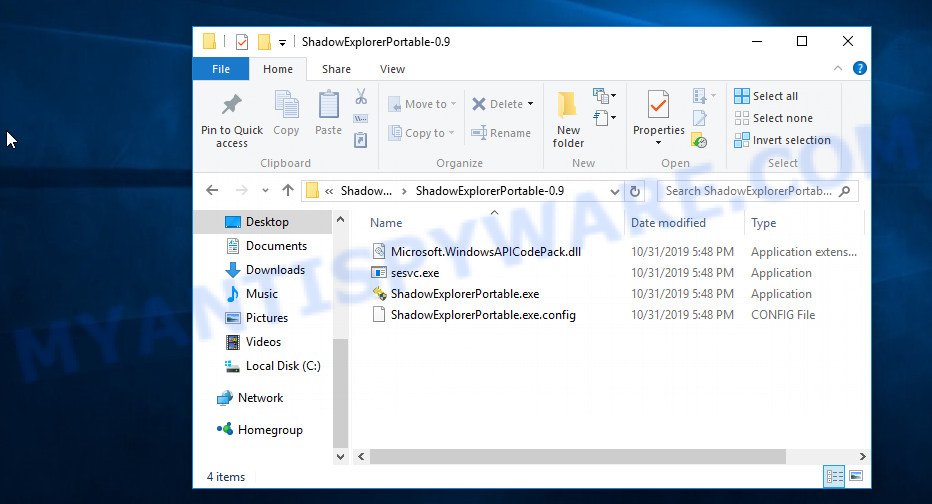
Find the ShadowExplorerPortable file and run it. You will see the main window of ShadowExplorer similar to what is shown in the picture below.
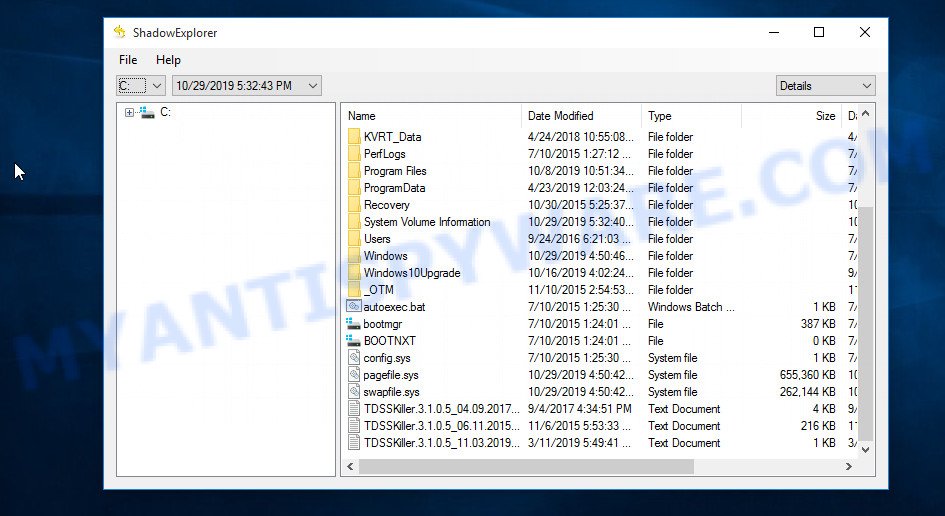
In the upper left corner of the window, select the drive on which encrypted files are located that you want to recover. Then, slightly to the right of the drive name, select the recovery point that is before the moment the files were encrypted.
On right panel look for a file that you wish to recover, right click to it and select Export as shown on the image below.
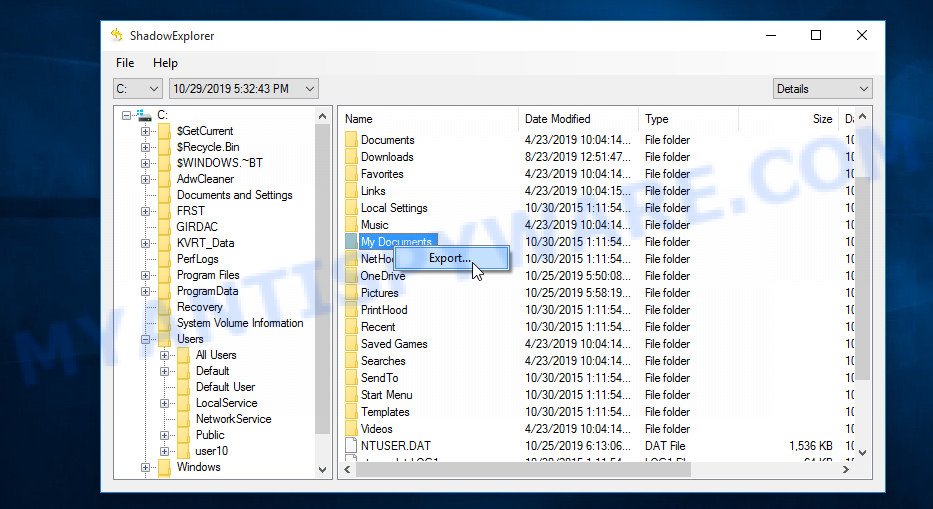
Now select the directory where the recovered files will be saved, then click OK button.
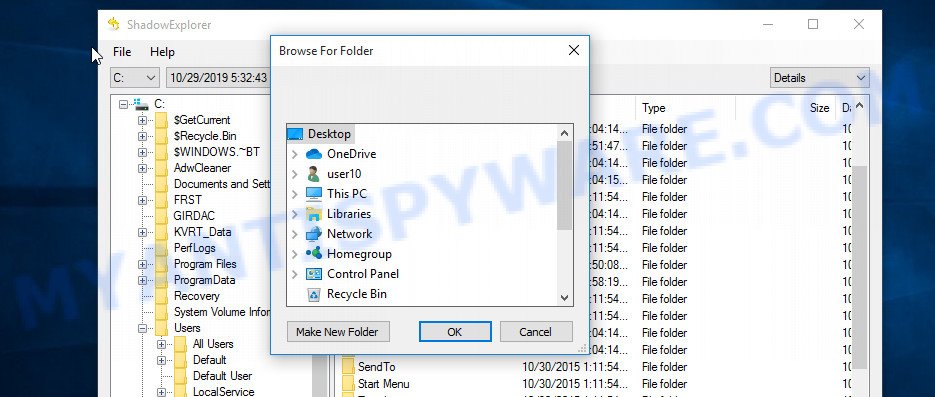
Unfortunately, ransomware often deletes all Shadow copies, and this blocks the ability to use the method described above to recover encrypted files. Therefore, if ShadowExplorer did not find Shadow copies (the field in which the recovery points are listed is empty), then all Shadow copies have been deleted. In this case, you have only one option left, to use data recovery tools. This method of recovering encrypted files is described below.
This video tutorial will demonstrate how to Recover encrypted files from Volume shadow copies using Shadow Explorer.
Recover encrypted files using Photo Rec
Data Recovery Utilities is your last chance to recover encrypted files. Why data recovery tools can help recover encrypted files? Before encrypting the file, some types of ransomware copies its contents to the computer’s RAM, encrypts it, then deletes the non-encrypted file, and writes the encrypted file to the hard disk. In reality, not-encrypted files are not physically deleted; they are simply marked by Windows OS as deleted. Data recovery software scan the computer’s hard drive for such files, and then restore them.
PhotoRec is a free data recovery tool that can help you recover encrypted files. This program has all the necessary functions and is absolutely free. In addition, PhotoRec has repeatedly proven its effectiveness. With its help, many users were able to recover the contents of encrypted files.
Download PhotoRec on your machine by clicking on the link below.
After the file download is completed, open the directory where you saved the file. Although PhotoRec does not require installation, but since it is delivered in the archive, you must unpack the archive before using it. Right click to testdisk-7.x.win and select Extract all. Follow the prompts. By default, the program will be unpacked into a new directory, which will be created in the directory where the downloaded file is located. When unpacking is completed, you will see a new directory with the name testdisk-7.x, open it.
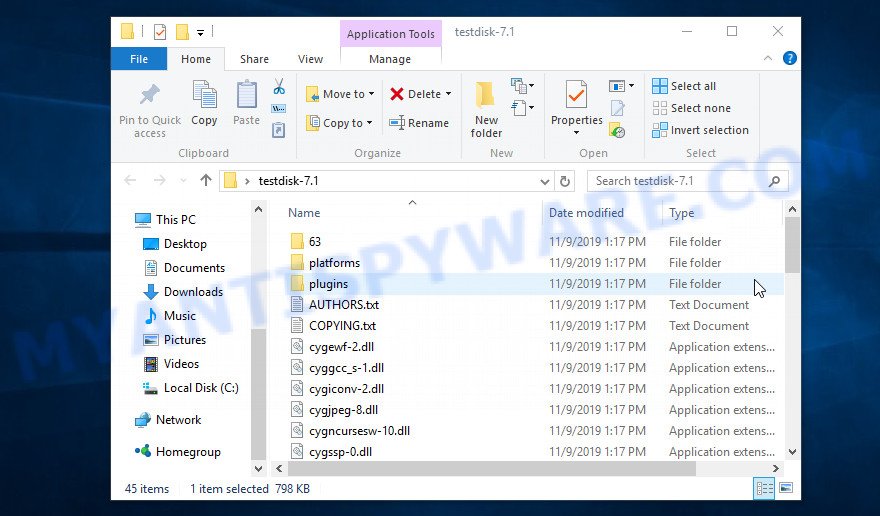
Scroll down the directory until you find a file named qphotorec_win. Run it. You will be shown the main program window as on the image below.
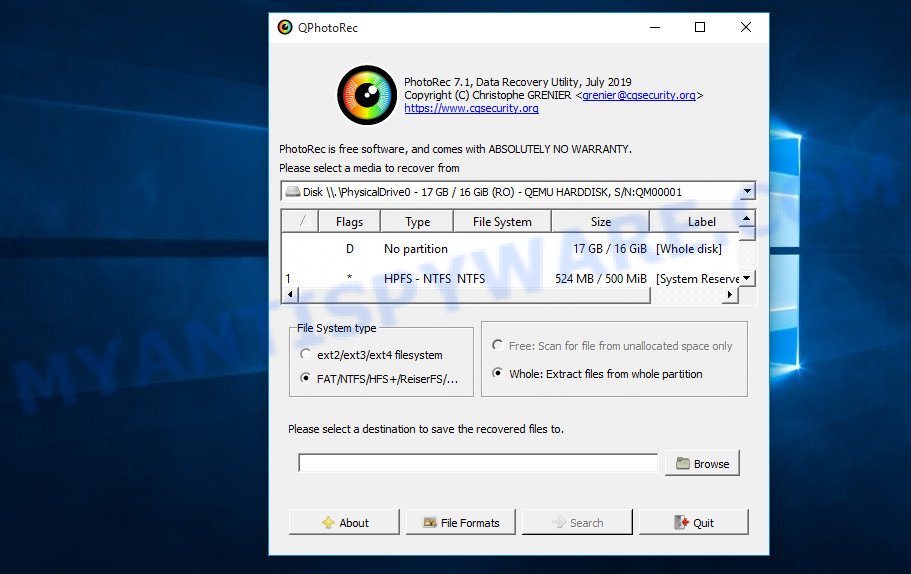
Find the box that is signed by “Please select a media to recover from”, right-click on it and select the device on which the encrypted files are located.
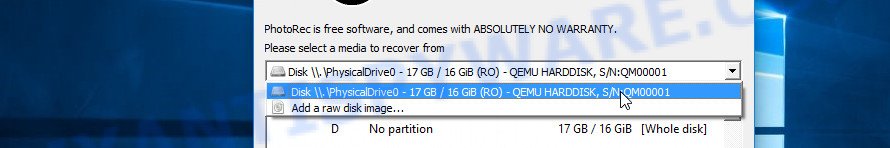
PhotoRec will scan the partition table of the selected device and show a list of partitions in the list. Select the partition from which you want to start the recovery of encrypted files. Be careful, pay attention to the type of partition (usually NTFS) and its size. Skip sections marked ‘System Reserved’.
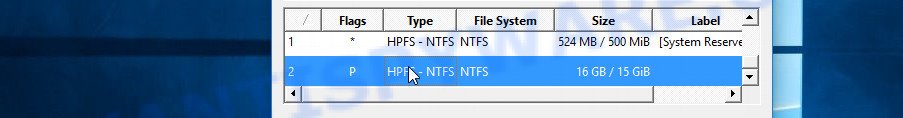
Having decided where PhotoRec will look for unencrypted files, now you need to select the types of files you want to restore. Click File Formats button, a small window opens with a list of file types that PhotoRec has the ability to find and restore. We advise you to leave only those types that you really need, so you will significantly speed up the process of searching and restoring files. After you make your choice, click the OK button.
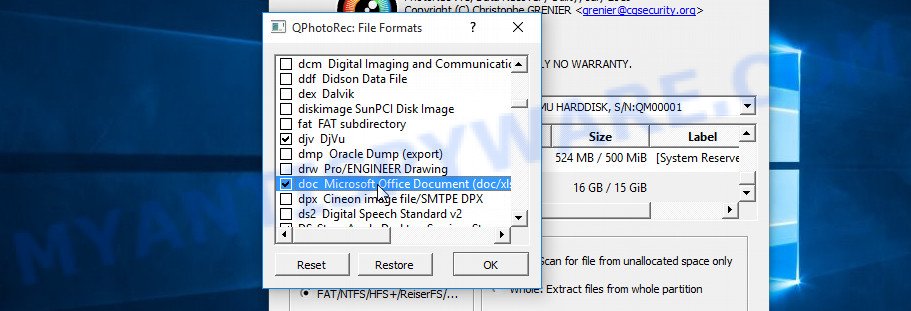
And lastly, click on the Browse button and select where the recovered files will be written. We highly recommend that you select an external drive, flash drive, or a separate section of the internal drive. If you restore files to the same disk on which you are looking for them, then the restored files will overwrite files that have not yet been found, which will block the ability to restore their contents.
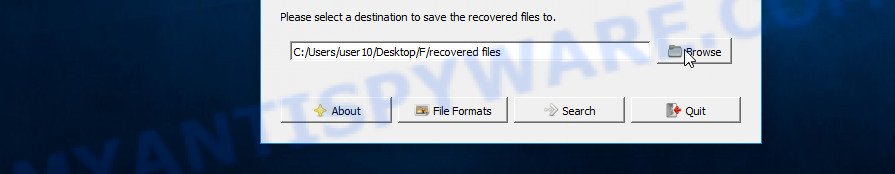
Now you can start file recovery. Just click the Search button. The program will start searching and restoring files. PhotoRec will open a window in which information on the count of recovered files will be updated in real time.
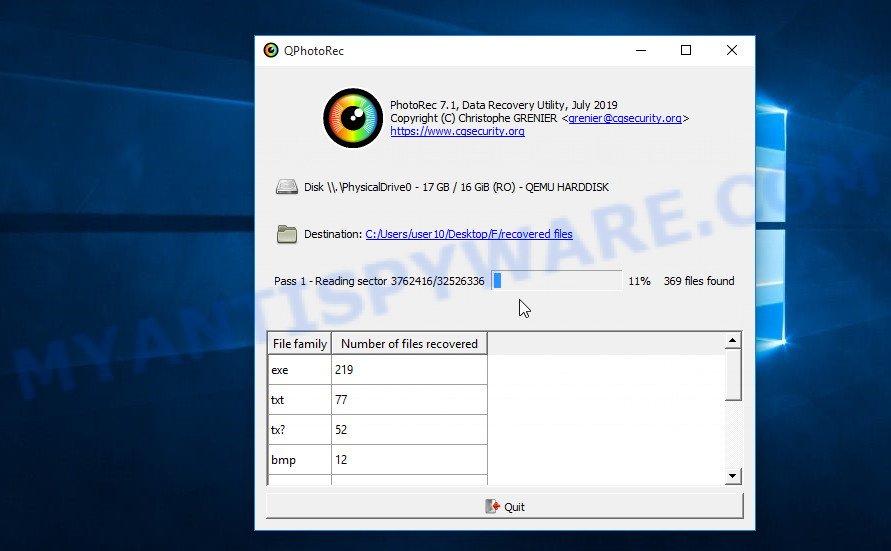
All files that were restored are written to the directory that you specified above. When the file recovery process is completed, press the Quit button. Open the directory where the recovered files were written. You will see something like the following.
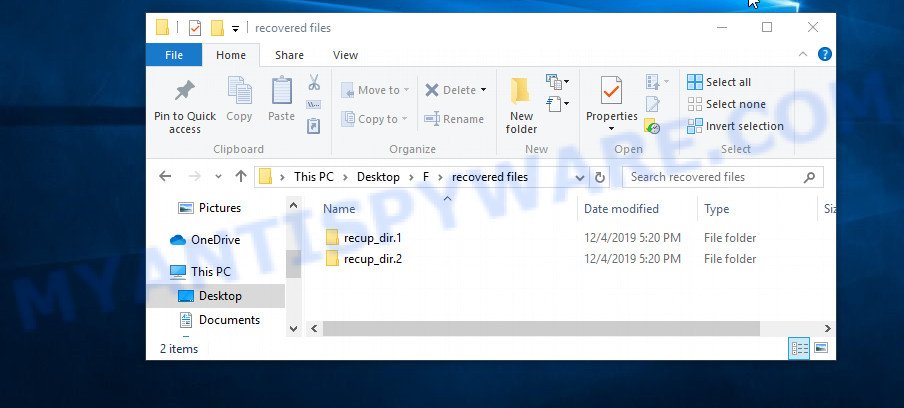
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your restored files by filename, extension and/or date/time.
This video tutorial will demonstrate how to Recover encrypted files using PhotoRec.
Finish words
This manual is designed to help ransomware victims recover encrypted files for free. If you have any questions or comments, then write to us. If you need help, please ask your question here.











how do i recover files and data corrupted by ransomware? all file types have been changed to .piiq files?
i am infected with ransomware that have a .zzla extension!
Any help for that?
crypted all my files ,photos and videos
also shown the emsisoft decryptor for stop Djvu results error
the remote name could not be resolved: ‘decrypter.emsisoft.com’
try using VPN or another internet provider
How to decrypt .zzla and .wwka files? tried everything and nothing works. seems like online encrypted
Tell me if u have any idea to remove wwka virus my laptop all file crupt plz help bro i do all youtube ideas but not work
Hye.. i have attacked by .gujd ransomware.. plz help me.. how can i encrypt.. also a few ppl online are suggesting ppl on instagram.. and when i talked to them.. they were like they can provide me with some kind of de-encryptor.. will that work?
this is a scam, these people will sell the decryptor from the creators of the virus (and they will raise the price), or promise to decrypt the files at a low price, and then, after receiving money from you, they will disappear.
My PC Files are Encrypted with Ransomware “GUJD” I tried decrypt_STOPDjvu with no luck but I did find this fie left on my pc from the attack. Has it got to do with the decryption key?
File Name “bowsakkdestx.txt”
{“public_key”:”—–BEGIN PUBLIC KEY—–\\nMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAt03ZcHQzGlZCQEwrRfm6\\nurctuhuLKqcapHV98TtailqAmUFUlaYIgGTzn81HPyvMOIH1WVa8lRYnBPR2iAy8\\n2YBA0YGIaJf7UVdadBdzrJG676\/p\/VMvywFfxWicc9GpqMofEOPx+eESdS1XXRME\\n\/ny0\/1i6JUP6tUmxrq2mIOhsJGw1VmEHmd5Z77e8QzAv8aYVnUbKt2cnWy8Kalkn\\nyqs8Sq3Lx4jp7L5L\/lcZGlHiWxXenI\/un26TpmxmT2Rr5N2bTfNaDyUHerPL62Fs\\nFveitASqlgBpE0SKIejzWZHxzODZg7tN8wjugtifxdegP3ncudqQrEsYP5AKx4eb\\n1QIDAQAB\\n—–END PUBLIC KEY—–\\n”,”id”:”YnaeTWb5G6ohNqsMoEBeYazAXbfeYQ0EzIjRujhz”}
pls help me recover my files. they are are corrupted by MOQS malware with an online key and none of these methods are working and i don’t have any backup. The photoRec only recovers the data which was previously deleted and shadow explorer is not working since there is no previous backup.
If the files are encrypted with the online key, they cannot be decrypted. There are no other recovery methods other than those described in this article (ShadowExplorer and PhotoRec). Therefore, I advise you to back up your important files and wait until decryption becomes possible. This can happen in a year, two years, or even never. Follow the news on our website or in our Facebook/YouTube account.
Shadow Explorer does not detect any files in in External HDD
Hello!
i need help how can i decrypt my files i have been attacked and all the files have been change the extension to .orkf
HELLO,
i need help to decrypt my file been change to extension .ridg
help me hhow to decrypt and restore my files
it is online key
Use the following guide: https://www.myantispyware.com/2021/09/27/how-to-remove-rigd-ransomware-decrypt-rigd-files/
Dear sir I’m facing ooii extension file issue when I tried emsisoft decrytor it says could not be resolved…please help me out any solution is there for my data
Use the following guide: https://www.myantispyware.com/2022/02/22/how-to-remove-ooii-ransomware-decrypt-ooii-files/
Dear sir if i decryption below mention messages come pls help me
File: C:\Encrypted\Akka.doc.tisc
Error: No key for New Variant online ID: 4gEQ8clnS4AdlXYCulRE7hepPS7jPuqBVKRAedZI
Notice: this ID appears to be an online ID, decryption is impossible
File: C:\Encrypted\SAM_2120.JPG.nqsq
Error: No key for New Variant online ID: 4gEQ8clnS4AdlXYCulRE7hepPS7jPuqBVKRAedZI
Notice: this ID appears to be an online ID, decryption is impossible
My system was attacked by Ransomware yesterday & all the files in the system were encrypted as NQSQ files.
There is a file created in my system that mentions I need to pay $980 to recover/decrypt my files.
help me how to decrypt and restore my files
it is online key
How do i get an online key to encrypt my filse attacked by .maql
How do i decrypt For an online key for .maql files
If the files are encrypted with the online key, they cannot be decrypted. If the methods described in this article did not help you, then I advise you to back up your important files and wait until decryption becomes possible. This can happen in a year, two years, or even never. Follow the news on our website or in our Facebook/YouTube account.
How to Decryptor Cool Files
Error: No key for New Variant online ID: 1b01S8Cf5AOr9qHqHAJJiZtH5XTn6pWQheMCGanj
Notice: this ID appears to be an online ID, decryption is impossible
The “1b01S8Cf5AOr9qHqHAJJiZtH5XTn6pWQheMCGanj” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Dear Friend
Please Help Me!
Ransomware virus in my computer is now clean, but are files are encrypted so please help me and send me decryptor of .piiq
Thanks
best regards
Use the following guide: https://www.myantispyware.com/2021/06/27/how-to-remove-piiq-ransomware-decrypt-piiq-files/
Myantispyware team
plz help me and guide me how to decrypt .pezi files
i also booted with new windows
I have a question, in any cases, will be an opportunity in the future to recover from dos encrypted malware? To recover a higher percentage or all of them, I ask this, because if there is a minimum chance that this will happen, I wont deleted those encrypted files.
I got infected by .qdla.
There is a small chance, but when decryption will become possible is unknown. Follow the news on our website or Facebook/YouTube channel.
Por favor ayuda
tengo mis archivos encriptados con el virus ransomware miia
Gracias
Use the following guide: https://www.myantispyware.com/2021/12/31/how-to-remove-miia-ransomware-decrypt-miia-files/
Sir,
Please Help Me!
Ransomware virus in my computer is now clean, but are files are encrypted so
i need help to decrypt my file been change to extension .utjg
help me how to decrypt and restore my files it is online key
Use the following guide: https://www.myantispyware.com/2021/11/16/how-to-remove-utjg-ransomware-decrypt-utjg-files/
Hi!
I got attacked by a DJVU ransomeware and ALL my filed got encrypted into .qdla. I’ve tried Emisisoft and ShadowExplorer, but it didn’t work. so do i just let my files destroyed to trash or there is something that I can do with it to decrypt?
I’ve killed all the viruses and malwares, so it won’t be back again.
Thanks
Sir, help me plz
how can i decrypt .maiv
Your personal ID:
0385UIhfSdG1OoVvHkiPKe9F9UTGTf9gPLlEGR9jPg8uykNXzb
The “0385UIhfSdG1OoVvHkiPKe9F9UTGTf9gPLlEGR9jPg8uykNXzb” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Is there any way to decrypt my files infected with extension qqqw?
Use the following guide: https://www.myantispyware.com/2022/01/25/how-to-remove-qqqw-ransomware-decrypt-qqqw-files/
Por favor ayuda
tengo mis archivos encriptados con el virus ransomware uigd
Gracias.
I need help with my personal ID
dYUDKE4rrBmSPsf8srHMsyP40jle9uyxDDCfdxt1
Your files are encrypted with an offline key. Therefore, first try the EmsiSoft decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec. If these free tools did not help to recover encrypted files, then you just have to wait for the moment when decryption becomes possible. Follow the news on our website.
Hello, my partition on the PhotoRec isn’t shown as the above: EFI system, MS Reserved, MS Data, and Windows Recovery Env (split into 3 sizes). So which one that contain the NTFS?
ID:0453JbdiohjkFuyYGu9EqopWIBJl29WIFlrv7nzjNmaAxALza
How to decrypt it.
I need help with my personal ID
nt0jroKkg7EBU5sTqFhyx2ReZFxjNBwgKCdXuRt1
Your files are encrypted with an offline key. Therefore, first try the EmsiSoft decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec (How to recover encrypted files). If these free tools did not help to recover encrypted files, then you just have to wait for the moment when decryption becomes possible. Follow the news on our website.
Please help, the files are locked with HESE virus and I can’t unlock them. I get a message that there is no online key ID. What am I doing? Thanks in advance
I need help with my personal ID: 4O5McKuX1wM6dhq0EnGQWamo8CTUKSqOZ7Xq3LeM
The “4O5McKuX1wM6dhq0EnGQWamo8CTUKSqOZ7Xq3LeM ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.